SMS spoofing is a common cyberattack. Fraudsters use specialized software to manipulate the SMS sender ID, making it as though the message is coming from a legitimate source, such as the bank. In this way, they can steal sensitive information or download malware onto the recipients’ phones.

It can be challenging to distinguish between legitimate and spoofed messages. To protect yourself, it's crucial to remain vigilant and cautious when responding to unsolicited SMS. Here are some common examples of SMS spoofing:
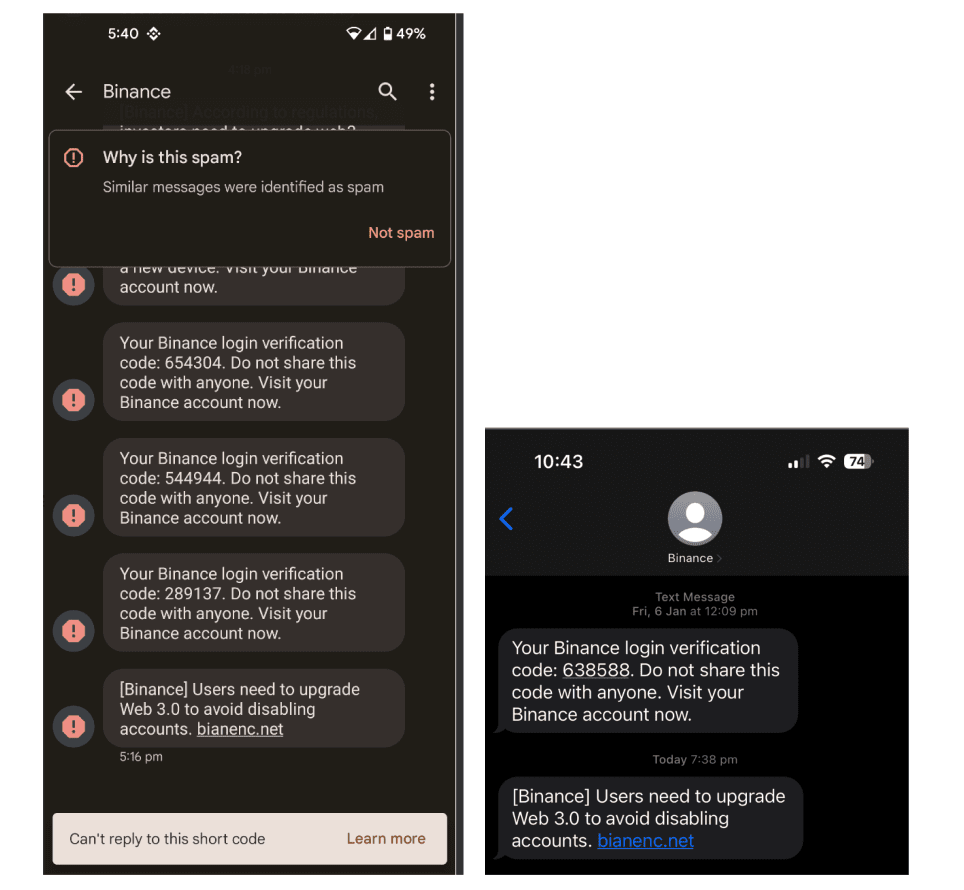
The most common type of spoofing is replacing the sender ID with a reputable business’’ number or name. For example, scammers would impersonate Binance or TrustWallet to send phishing SMS. These SMS would be grouped under the same thread as the official messages, like 2FA codes. This is because the hackers used SMS spoofing to manipulate the sender ID and disguise the actual source of the message.
Scammers would claim that the recipient has won a prize. They would then ask for the recipient’s bank details so they can deposit the winnings or visit a link to claim the prize.
This involves sending threatening or inappropriate messages to intimidate their victims, hoping to extort money from them. For example, threatening to ban the user’s account. Hackers often take advantage of your fear of losing assets. In this situation, you should remain calm and verify the message before acting.
For example, here’s a list of suspicious phishing websites impersonating Binance.

A Binance user received an SMS with the sender name “Binance”, asking them to upgrade their account to continue using Binance service.
Hackers used specialized software to manipulate the SMS sender ID, making the fake SMS appear as though it was legitimately coming from Binance. As the fake SMS was under the same thread as the official 2FA code messages, the user assumed that the message was legitimate. After they logged in to the phishing website, their account credentials were stolen by hackers.
Another Binance user received a fake SMS to confirm a withdrawal. The user thought the message was legitimate and logged in to their account on the phishing website to “cancel the withdrawal request”.
After obtaining the user’s credentials, the hacker initiated a withdrawal request from their account and guided them to enter the 2FA code on the phishing website. After the user entered the code, the hacker withdrew their assets successfully.
Some learning from this example:

Several Binance users received an SMS with a link to verify or upgrade their accounts, which was a phishing attempt to steal their account credentials.


The phisher may claim ‘new login’ and for you to call back to a suspicious phone number, or declare personal data via a suspicious URL.

Do not call or click any of the sources provided. You can use Binance Verify to check the legitimacy of any Binance communication. For more information, please visit What is Binance Verify?
If you come across any scam activity phishing as Binance, please report it immediately to our team.