The building is quiet in the way offices get quiet when they’re pretending nothing can go wrong. One person at a desk that still has yesterday’s coffee ring on it. A dashboard on the left screen, a reconciliation sheet on the right, and a small number that does not belong. The transfer is supposed to land clean. It lands close. Not close enough. The kind of gap you can explain in a meeting, but not the kind you can ignore and sleep. You zoom in. You refresh. You check the fee schedule again even though you know it by heart. The chain keeps moving while you stare at it, and you feel the old, familiar unease: not fear of losing money, exactly, but fear of losing the right to say “this is reliable.”
This is where slogans die. Not in public, not with drama, but privately, under fluorescent light. “Real-world adoption” sounds harmless until it becomes wages. Until it becomes payroll files and contractor invoices and retainer contracts with clauses that don’t care about your intent. A chain can be fast and still fail the moment someone depends on it to be boring. A chain can be “public” and still fail the moment a client asks for a report that stands up to scrutiny, not enthusiasm. The adult world doesn’t reward good narratives. It rewards systems that keep their promises quietly and repeatedly.
You learn this through procedures, not theory. The compliance call that starts on time, ends late, and has that one silence in the middle where everyone is doing the math in their heads. The treasury review where the person who signs off never jokes, because joking is how you admit you’re not sure. The audit prep folder that grows into a small library because “we have logs” is not the same as “we have evidence.” The late-night monitoring rotation where you start naming your graphs like people because you stare at them long enough. The pressure is not cinematic when it’s yours. It’s a tightness in the chest when you see an anomaly, and a heavier tightness when you don’t.
There is an old confusion in this space that only becomes obvious when money starts behaving like responsibility. People say “public” as if it means “true.” As if visibility is a substitute for proof. Public is just exposure. It’s who can see what, and how long it stays there. Provable is different. Provable is what you can defend when a skeptical party is paid to assume you’re wrong. And when you’re dealing with wages and contracts and brands, privacy isn’t always a preference you toggle. Sometimes it’s a duty. A legal duty. A contractual duty. A human duty, if you’ve ever watched what happens when salary data leaks or vendor terms get dragged into daylight.
Auditability, though, is non-negotiable. If you can’t show what happened, why it was allowed, and who had the authority, you’re not running a system. You’re running a rumor. The trick is that the adult world demands both: confidentiality and accountability. Not “privacy because secrecy feels cool.” Not “transparency because it sounds righteous.” Both, because the real world punishes the absence of either.
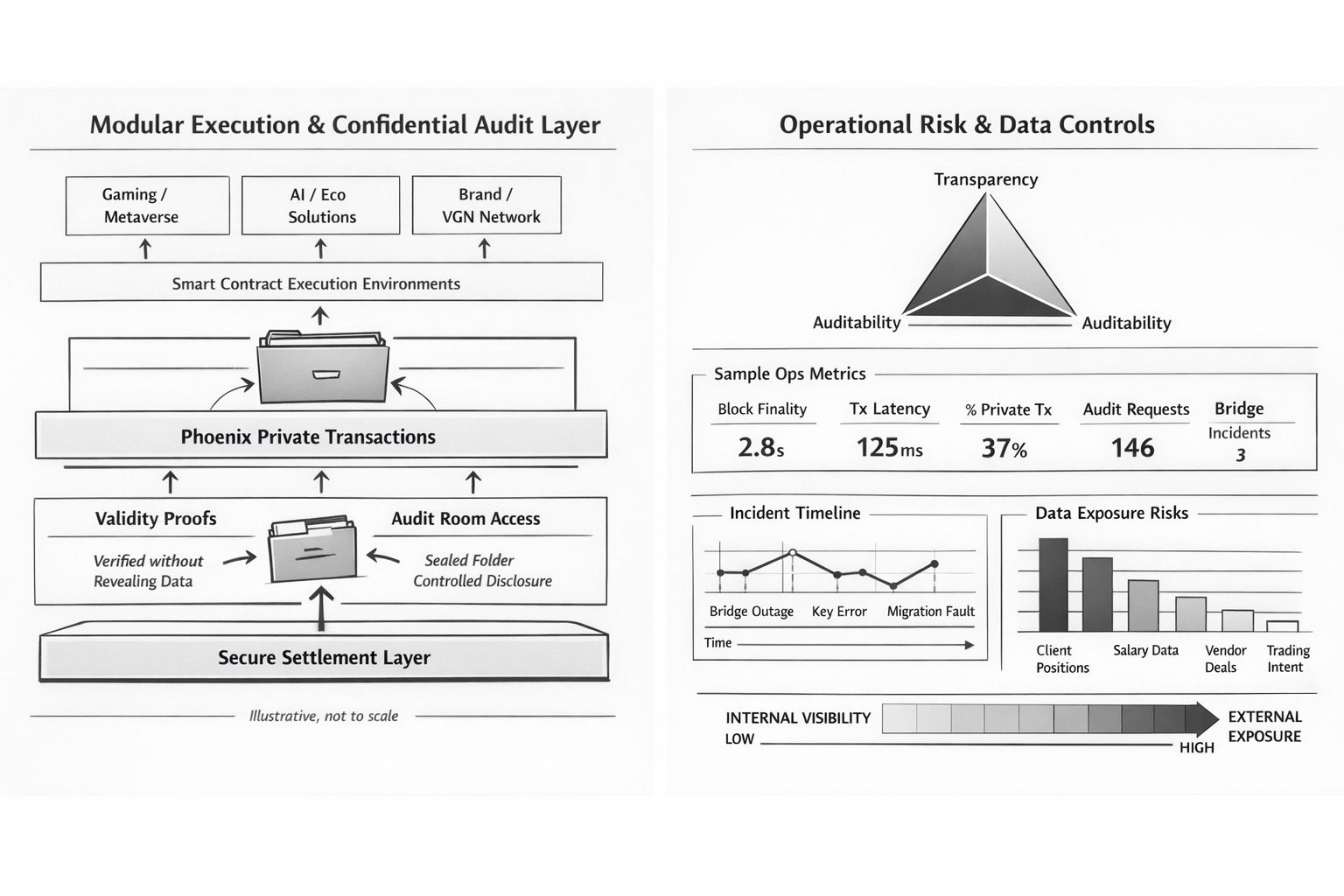
So the question becomes practical. Can the ledger verify correctness without turning every detail into permanent public gossip? Can it speak with authority when it needs to, and shut up when it should? Not in a vague moral sense. In the literal sense: who can see what, under what conditions, with what evidence that the view is complete and consistent with the rules.
The metaphor that keeps making sense is plain. A sealed folder in an audit room. It contains everything required, nothing extra. It’s sealed under procedure. It is not opened because someone is curious. It is opened because someone has standing. An auditor. A regulator. Compliance. Maybe a court order. When it opens, it opens fully, under rules. When it closes, it closes. There is a record that it opened at all. That’s not secrecy. That’s adult handling of sensitive facts.
Phoenix private transactions fit that logic if you treat them as audit-room discipline applied on-chain. Not magic. Not vibes. More like a system that can prove “this was correct under the rules” without shouting every ingredient to the street forever. You don’t need the entire internet to know your vendor cadence, your treasury timing, your internal rebalancing, your client terms. You do need a way to prove, later, that the payment was legitimate, authorized, consistent with policy, and not rewritten after the fact.
That distinction matters because indiscriminate transparency has teeth. It doesn’t just “increase trust.” It can destroy it. It exposes client positioning and negotiation leverage. It exposes salaries and bonus cycles and, with them, the kinds of resentment that don’t show up in metrics until it’s too late. It exposes vendor relations—who you pay early, who you pay late, who you’re dependent on. It exposes trading intent before execution, and that’s not philosophical harm; it’s market harm, the kind that turns into an incident report and then into a lawsuit. It exposes patterns that attackers love: when keys move, when people are tired, when the process is brittle and everyone is relying on memory instead of checklists.
If you’ve sat through enough postmortems, you stop believing in graceful degradation. Trust doesn’t degrade politely—it snaps. The snap is usually small at first. A discrepancy. A missed reconciliation. A partner asking an uncomfortable question. Someone forwarding a screenshot of something that should never have been public. A bridge pause that lasts longer than promised. People don’t leave when they’re angry; they leave when they’re uncertain.
Which is why architecture stops being aesthetics. It becomes containment.
Vanar’s framing—modular execution environments over a conservative settlement layer—sounds like a diagram until you’ve lived the alternative. Settlement is where obligations become final. Where disputes end. Where the thing you did has consequences you can’t hand-wave away later. Settlement should be boring. Dependable. Conservative. The part you can point to and say, “This is the anchor, this is the record, this doesn’t get clever.” Execution is where builders work, where products live, where speed is felt and features ship. Keeping them separable is not a design flex. It’s how you stop a noisy, fast-moving environment from contaminating the layer that must behave like a contract.
This matters more when your surface area isn’t small. Vanar isn’t pretending it’s building for one narrow tribe. The team’s experience across games, entertainment, and brands brings a specific kind of operational pressure: peaks that don’t ask permission, reputational risk that spreads faster than patches, partners who don’t accept “it’s decentralized” as an excuse, consumers who will not wait. A metaverse product like Virtua Metaverse doesn’t get to fail gracefully. A games network like VGN games network can’t ship an update and then discover the infrastructure leaks more metadata than promised. “Next three billion consumers” is not a poetic goal. It’s a liability profile. It means mainstream expectations: privacy norms, regulatory scrutiny, customer support tickets, and the quiet, relentless demand that the system works when nobody is thinking about it.
EVM compatibility fits here in a way that is less romantic and more useful. It reduces operational friction. It reduces the number of novel failure modes. It means developers bring familiar patterns. Security teams bring familiar tools. Auditors bring familiar mental models. Incident response becomes faster because you’re not reinventing the vocabulary of what went wrong. Every custom stack adds a new class of mistakes, and mistakes don’t show up one at a time like polite visitors. They come in clusters: during migrations, during launches, during weekends, during the one week someone important is off-grid.
The real sharp edges are not in the whitepaper. They’re in the handoffs.
Bridges and migrations are where your architecture meets fatigue. ERC-20 and BEP-20 representations moving to native assets is not just “user onboarding.” It’s a moment where the chain either demonstrates operational maturity or it doesn’t. The chokepoints are familiar to anyone who’s had to write the postmortem: a relayer misconfigured, a stale allowlist, an upgrade that didn’t propagate to monitoring, a “temporary” multisig signer set that stayed temporary because nobody wanted to schedule the ceremony again. An address pasted into the wrong field at 03:40. A key rotation delayed because two signers were asleep in different time zones and the escalation path was unclear. A brittle process that depended on one calm person being awake, and that calm person is human.
Key management is where the whole system becomes very small. It collapses into hands, habits, and places people store secrets. You can build a beautiful ledger and still lose credibility because someone handled recovery like it was a theoretical feature. Adult controls are boring for a reason: permissions that are explicit, disclosure rules that are written down, revocation that actually revokes, recovery that has been rehearsed, accountability that survives staff changes. It’s not glamorous to say “we have a procedure.” It’s glamorous to ship. But procedures are what keep shipping from turning into a weekly apology tour.
This is where compliance language becomes part of engineering reality. MiCAR-style obligations are not a mood. They are the shape of an ecosystem that is trying, slowly, to become legitimate enough to touch regular people’s money. The closer you get to brands, payroll, and regulated partners, the more your architecture becomes part of your compliance story. Not because you want to impress regulators. Because regulators and auditors need systems that can be examined, supervised, corrected, and held accountable. If you can’t explain your controls in their language, you end up explaining your failures in their language, and that is always worse.
Treating VANRY as responsibility instead of price talk changes how you build. Staking is not a decoration if it acts like a bond. A bond is not there to make you feel brave. It’s there to make you careful. Skin in the game becomes accountability when participants have something to lose for negligence, for downtime, for dishonesty. When you ask builders and users to trust execution, you must also design a system where those who secure and operate the network are bound to consequences. Not performative consequences. Real ones.
Long-horizon emissions, in that frame, read less like an incentive schedule and more like patience encoded. Legitimacy takes time. Integrations take time. Regulation takes time. Real adoption takes time because the real world moves at the speed of contracts and review cycles and risk committees. A system that assumes immediate maturity is not ambitious. It is unprepared. A system that accepts a long horizon is admitting something honest: this is going to be built under scrutiny, with iteration, with boring improvements, with controls that get tighter over years, not weeks.
The monitoring screen at 02:11 doesn’t care about philosophy. It wants the discrepancy explained. It wants a trace that ends cleanly. It wants the runbook updated so the next person doesn’t repeat the same mistake under the same fatigue. That’s the only kind of writing that matters in the long run: the notes that prevent recurrence.
And yet, if you stay in operations long enough, philosophy shows up anyway, not as poetry but as a simple conclusion you keep arriving at from different angles. A ledger is not a stage. It is an operating system for obligations. The best systems are not the ones that talk the most. They are the ones that know when silence is part of correctness.
So you build a chain that can prove what must be proven without turning every detail into permanent public theater. You build confidentiality with enforcement: validity without unnecessary exposure, selective disclosure to authorized parties with standing, complete and consistent when the sealed folder must be opened. You build modular execution so builders can move fast without shaking the foundation. You keep settlement conservative so it behaves like a contract should. You choose EVM compatibility not as a personality trait but as a reduction in ways to fail.
At the end of the night, there are still two rooms that matter. The audit room, where the sealed folder gets placed on the table and the system either produces coherent truth or it doesn’t. And the other room, quieter, where someone signs their name under risk—under payroll, under client contracts, under regulatory duties, under the promise that this network will behave tomorrow the way it behaved today. The work is not to sound confident. The work is to be defensible. The work is to keep speed without losing composure. The work is to build something that can carry real money without turning real people into collateral damage when a small discrepancy appears at 02:11.