In every blockchain, digital signatures are the base layer of security. They prove a transaction is real, that the person sending it owns the funds, and that no one can change it. On Dusk this becomes even more important because the network is built for privacy, confidentiality, and compliance. So Dusk does not just use normal public signatures. It uses signature systems that work with zero knowledge proofs and private transactions.
A signature scheme lets someone prove they own assets and approve an action without showing their private key. On Dusk, this process is tightly linked with confidential transactions. That means signatures must stay valid even when the sender, receiver, and amount are hidden. This requires signatures that can be checked by the network while keeping the data private.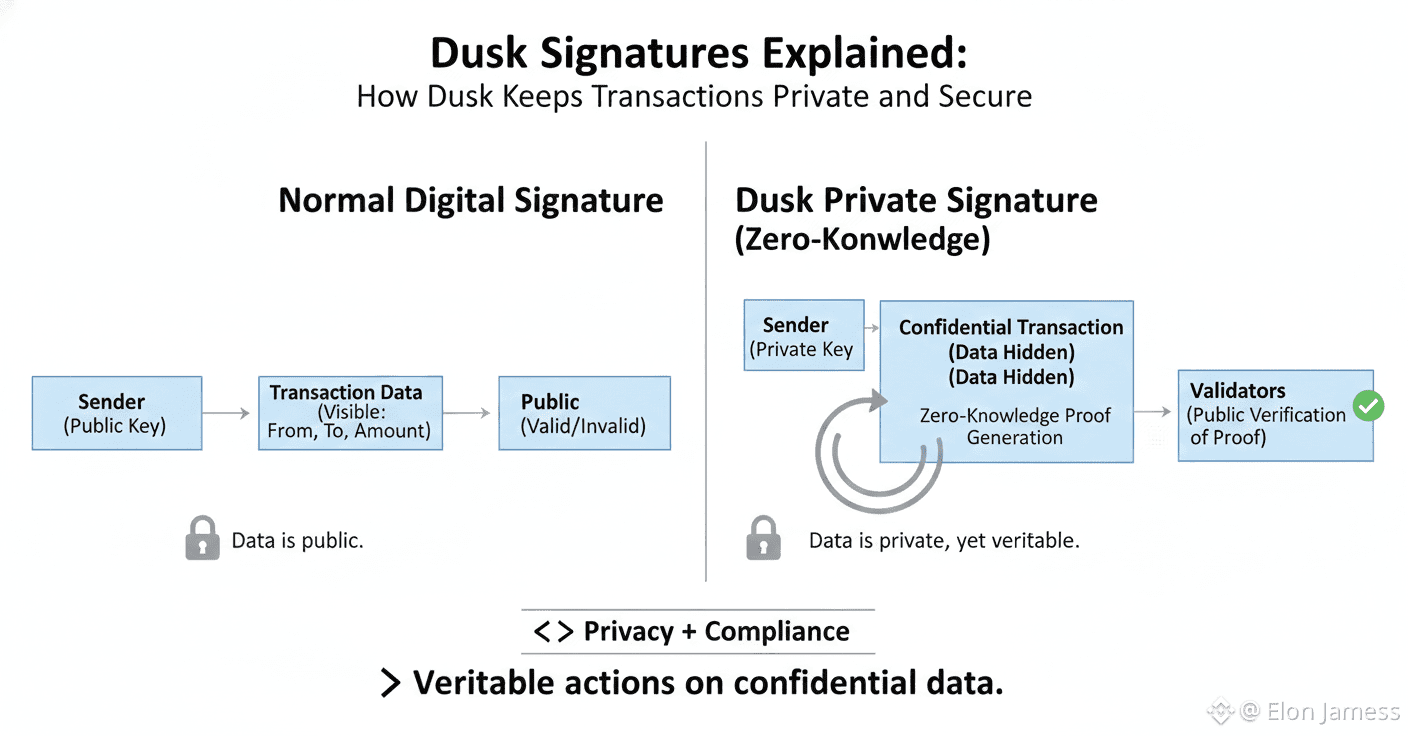
Dusk combines signature schemes with zero knowledge cryptography. When a transaction is created, the signer makes a cryptographic signature using their secret key. This proves the transaction is legitimate and the signer is allowed to spend the assets. Instead of showing all transaction data, Dusk puts signature verification inside zero knowledge proofs. This allows validators to confirm correctness without learning sensitive information.
This method is very important for institutions and regulated use cases. Banks and financial companies need strong proof that transactions are real and cannot be denied later. At the same time they must follow privacy laws like GDPR. Dusk signature schemes support selective disclosure, meaning transaction validity can be proven publicly while specific details can be shared only with authorized parties like regulators or auditors.
Another key part of Dusk signature design is compatibility with its Phoenix transaction model and UTXO based privacy system. Each transaction output is protected by cryptographic commitments and signatures, ensuring only the rightful owner can spend it. Even though outputs are confidential, the signature system makes sure double spending is impossible and state transitions remain consistent.
From a consensus point of view, signatures are also essential. Validators and generators use cryptographic signatures to authenticate blocks, votes, and consensus messages. This prevents attackers from pretending to be honest participants or injecting invalid data into the consensus process. By combining signatures with stake based incentives, Dusk strengthens Sybil resistance and overall network security.
So on Dusk, signature schemes are not just about proving identity. They are a core building block of private, compliant, and secure on chain finance. By integrating advanced signatures with zero knowledge proofs and confidential transactions, Dusk finds a rare balance. It provides strong cryptographic security, privacy by default, and verifiability when regulation demands it.


