This is the 1943th original issue of Vernacular Blockchain. Author | Contributor Compiler | Huo Huo Producer | Vernacular Blockchain (ID: hellobtc)
For a long time, blockchain has only been able to achieve two of the three impossible triangles (scalability, decentralization, and security). Therefore, after Ethereum achieved a high level of security and privacy, capacity expansion became a top priority. Therefore, Layer 2 was born. Among the current Layer 2 capacity expansion solutions, ZK technology is considered by Ethereum co-founder Vitalik Buterin (V God) to be the ultimate solution to the capacity expansion problem.
On May 21, at the non-profit annual global Ethereum conference EDCON 2023 held in Montenegro, Vitalik said that in the next 10 years, zk-SNARK, which uses ZK as the underlying technology, will be as important as blockchain.
So what exactly is zk-SNARKs, which is being promoted by Vitalik Buterin recently? What blockchain problems can it solve? Let’s take a look at today’s introduction. The following is the main text:
01 What are zk-SNARKs?
1. Who created zk-SNARKs?
The term “zk-SNARKs” was coined by a group of cryptographers, including Nir Bitansky, Alessandro Chiesa, and Eran Tromer, who initially published the basic principles of zk-SNARKs in a paper. Since then, zk-SNARKs have been developed and improved by many different projects and teams.
2. What does zk-SNARK stand for?
- ZK: zero knowledge
Zero-knowledge means that the person who is verifying the statement cannot gain any new information from the verification process. In other words, during a zero-knowledge proof, the verifier knows nothing except whether the statement is true or false.
- S is for simplicity
Succinct zk-SNARKs proofs are short and easy to verify proofs. This is in contrast to regular zero-knowledge proofs, which can be very long and complex. Typically, zk-SNARK proofs can be verified in milliseconds.
- N: non-interactive
Non-interactive zk-SNARKs proofs do not require any interaction between the prover and the verifier. This means that only a single result message is sent from the prover to the verifier. This is in contrast to interactive proofs, where the prover and the verifier must interact back and forth with each other to complete the proof.
- AR: argument
An argument is a reason or set of reasons that support a point of view. In the context of zk-SNARKs, a proof is a series of mathematical operations used to prove that a statement is correct.
- K:knowledge
Knowledge refers to the idea that the prover knows some information necessary to complete the proof. This could be the private key of an account, for example.
To summarize, zk-SNARKs is a ZK system (zero-knowledge proof system) that allows a user (the “prover”) to prove something to another party (the “verifier”), such as their identity, their ownership of funds, etc., without revealing any information about those assets. For example:
- The user should be able to prove that he has enough balance in his account to buy a product or service without having to share the exact amount he has; - The user should be able to verify his identity before accessing the application without having to share his personal data.
As an example of how to “explain zk-SNARKs to a 5-year-old”, here’s a game that explains what zk-SNARKs are:
“Imagine that you are playing “Where is the Chinese teacher?” with three friends. The prize is a $1,000 bet to be split equally between the winners. You and your friends sit around a table and each of you is given a picture with a Chinese teacher on it.
You must find the language teacher in the picture, and once you find the language teacher you need to prove that you found her, without revealing her location or any other information. In other words, you want to prove knowledge of the facts without revealing any information beyond the validity of your claim.
Using the zkSNARK primitive, you can take a piece of paper of the same size and mark a dot at the location of the Chinese teacher in the picture. You can then hide the paper in a box, and once your friend solves the puzzle, they can see for themselves where the Chinese teacher you marked is located.”
In other words, zk-SNARKs allow you to prove the verification information you need without revealing the specific value of that information. In the current cross-chain ecosystem, the use of zk-SNARKs technology can maintain the privacy of blockchains and DApps built on its platform. The key idea is that it is impossible for the verifier to obtain any information about the proof (hence the name "zero-knowledge" proof).
02 zk-SNARKs How it works
zk-SNARKs are particularly important in the crypto space because many blockchains are public in nature, making privacy particularly important. The most famous example is Zcash, a private crypto asset. When Zcash is traded on public blockchains such as Bitcoin and Ethereum, details such as the sender and receiver addresses, as well as input and output values (i.e., how much was spent and how much was not spent) are used for verification. But with zk-SNARKs, Zcash can prove that transactions are valid without disclosing information such as addresses and values.
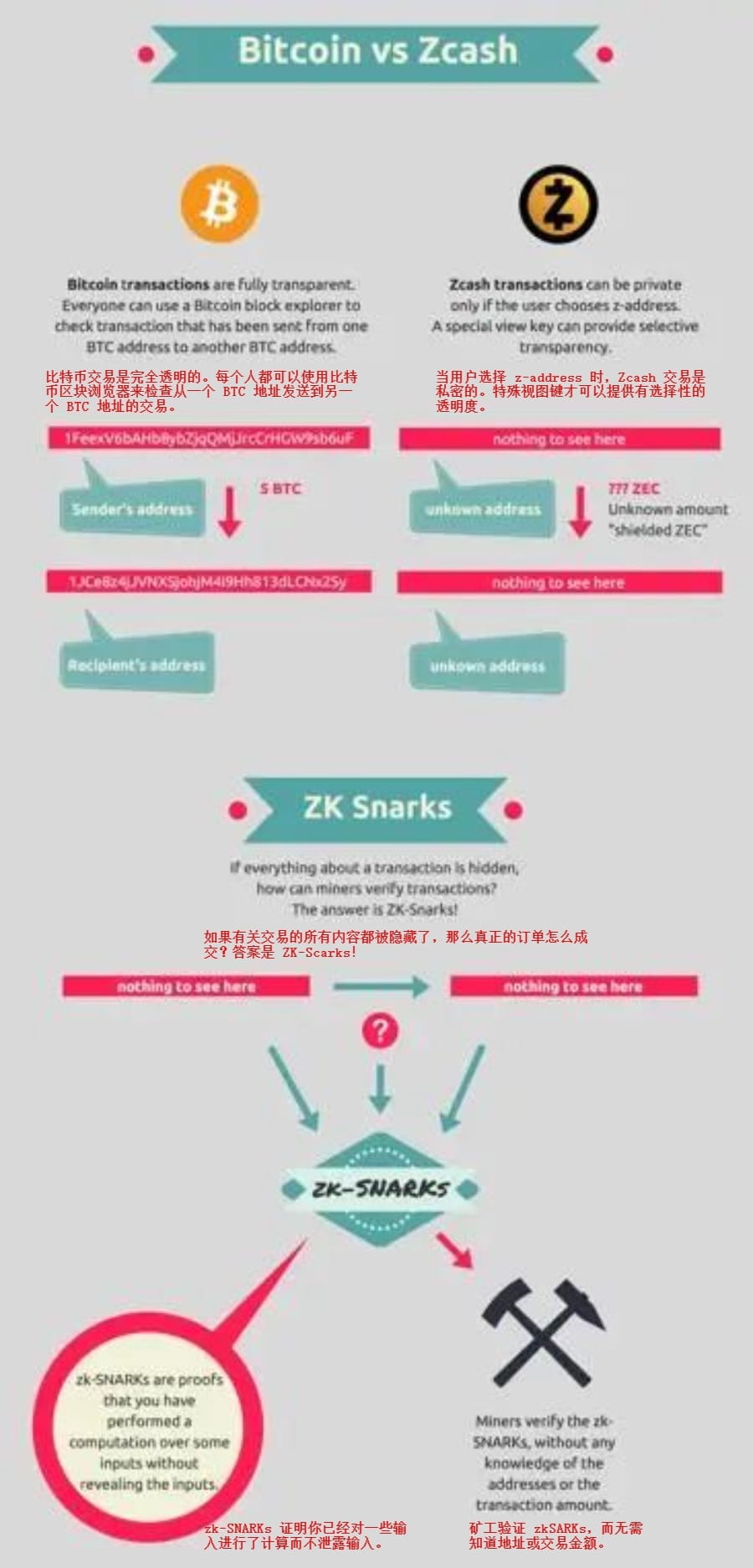
How Zcash uses zkSNARKS to provide a privacy layer for crypto users Source: Blockchainhub.net
How do zk-SNARKs work? Digital signatures form the working principle of zk-SNARKs. Digital signatures use cryptographic algorithms to protect sensitive information, keeping it hidden from another party while providing the party with the necessary proof requested. So how is it done specifically? Here are the steps: 1. The prover first generates a pair of keys, one public key and one private key. He signs the transaction using the private key. 2. The prover then encodes this transaction into zk-SNARKs, which is a mathematical proof that the transaction is valid. 3. The proof is sent to the verifier along with the public key. The verifier then uses the public key to check whether the formula is correct without knowing any other information about the transaction. Since only a small amount of information is verified, this check can be done very quickly to confirm that the transaction is valid.
03 Specific use cases of zk-SNARKs
1. Which tokens use zk-SNARKs?
SNARK crypto tokens are crypto assets that use zk-SNARKs to improve privacy, also known as privacy tokens. Examples of such privacy tokens are: - Zcash (ZEC) - Verge (XVG) - Monero (XMR) - Dash (DASH) - Beam (BEAM) - Horizen (ZEN) - Bytecoin (BCN) The main challenge with zk-SNARKs is that if the private key is compromised, forged proofs can be created. This could allow the creator of a forged proof to commit fraud, for example, creating and using fake privacy coins.
2. Other applications of zk-SNARKS
Filecoin is a decentralized storage provider whose operation involves multiple aspects.
First, there are storage providers on the Filecoin network (who provide storage space in exchange for block rewards), the “provers,” who must prove that they are storing data correctly on-chain. On the other hand, we have “validators,” or nodes, who must verify that the storage providers are storing and protecting the data correctly. These validators must be satisfied with the proofs given by the storage providers. This requires storage providers and nodes to communicate whenever data changes hands. As you can imagine, this process will be resource-intensive. “The amount of data that must be proven by a single storage provider in order to verify their storage is enormous today and will only grow over time,” the official Filecoin blog post explains. “The Filecoin network has a block time of 30 seconds. To keep that time constant and enable a scalable approach, Filecoin needs a solution that allows for fast, efficient, and robust verification,”
With zk-SNARKs, the Filecoin network can improve its scalability and efficiency by reducing the time it takes for parties to verify storage. For storage providers, zk-SNARKs reduce the amount of data they need to transmit to prove their storage, thereby reducing operating costs.
3. zk-SNARKs can also be used for other things such as:
- Authentication: Verify user credentials without a password, and eliminate the need for documentary proof such as passports and birth certificates to protect sensitive information such as place and date of birth.
- Voting system: Voter identity can be verified without identity verification, and even if the ballot is leaked, the voter's identity cannot be identified, thus protecting voter privacy.
- Data compression: This is an interesting use of zk-SNARKS and deserves its own section.
04 Summary
In general, there are three key points about zk-SNARKS: 1. zkSNARKS is a zero-knowledge proof system that allows one party to prove to another party that they know a value x without communicating any other information about x. 2. The key idea is that it is impossible for the verifier to deduce any information about x simply from the fact that the prover was able to prove that they knew x. This protects the prover's data privacy. 3. Zero-knowledge proof systems are used in a variety of applications, including secure communications, cryptography, and privacy-preserving data analysis. Although zero-knowledge proof systems are a relatively new field of research, there are still many unresolved questions about their feasibility and practicality. However, they have been used to create some impressive products.
What do you think about zk-SNARKs? Feel free to leave a comment in the comment section to discuss.
Original link: https://phemex.com/academy/what-is-zksnark Original title: What Is zkSNARK: A Beginner-Friendly Explainer Original author: Contributor Translator: Huo Huo
END



