Author: Decent Land Labs
Translation: Xiaosong HU @ Contributor of PermaDAO
Reviewed by: John Khor @ Contributor of PermaDAO
motivation
Many Web3 dapps, products, and protocols initially want to be fully decentralized and built using only on-chain components. However, when they face scaling challenges, introducing Web2 elements becomes a powerful solution to enhance scalability and user experience (UX).
A centralized Web2 architecture has significant benefits for scalability, but at the same time may sacrifice the core principles of Web3.
question
When a project incorporates web2 elements into its technology stack, it inherently begins to compromise some of the core principles of decentralization, including transparency, trustlessness, and verifiability.
To address this challenge, we introduce the Verifiable Atomic Computation Paradigm (VACP) and a real-time implementation of a Molecular Execution Machine (MEM).
This approach aims to maintain the integrity of the core decentralization principles while addressing scalability and user experience issues.
So, what is VACP?
The Verifiable Atomic Computation Paradigm (VACP) is made possible by the synergy of three components:
Lazy evaluation, pioneered by the SmartWeave protocol and 3EM.
Permissionless Verifiable Computation (VC) enables computations to be independently verified and executed without centralized control.
Leverage a tamper-proof data availability (DA) layer, such as Arweave, to ensure data integrity and availability throughout the process.
By combining these three essential elements, VACP provides a powerful framework for maintaining decentralization, transparency, and trustlessness while enabling scalable and verifiable computation for web3 developers.
Arweave plays a fundamental role as a cross-blockchain L0 layer, which enables VACP to operate seamlessly with multi-chain functions. VACP uses Arweave's data availability verification and KYVE protocol in combination to reliably ensure the integrity of data on various blockchains, thereby enhancing its versatility and reliability.
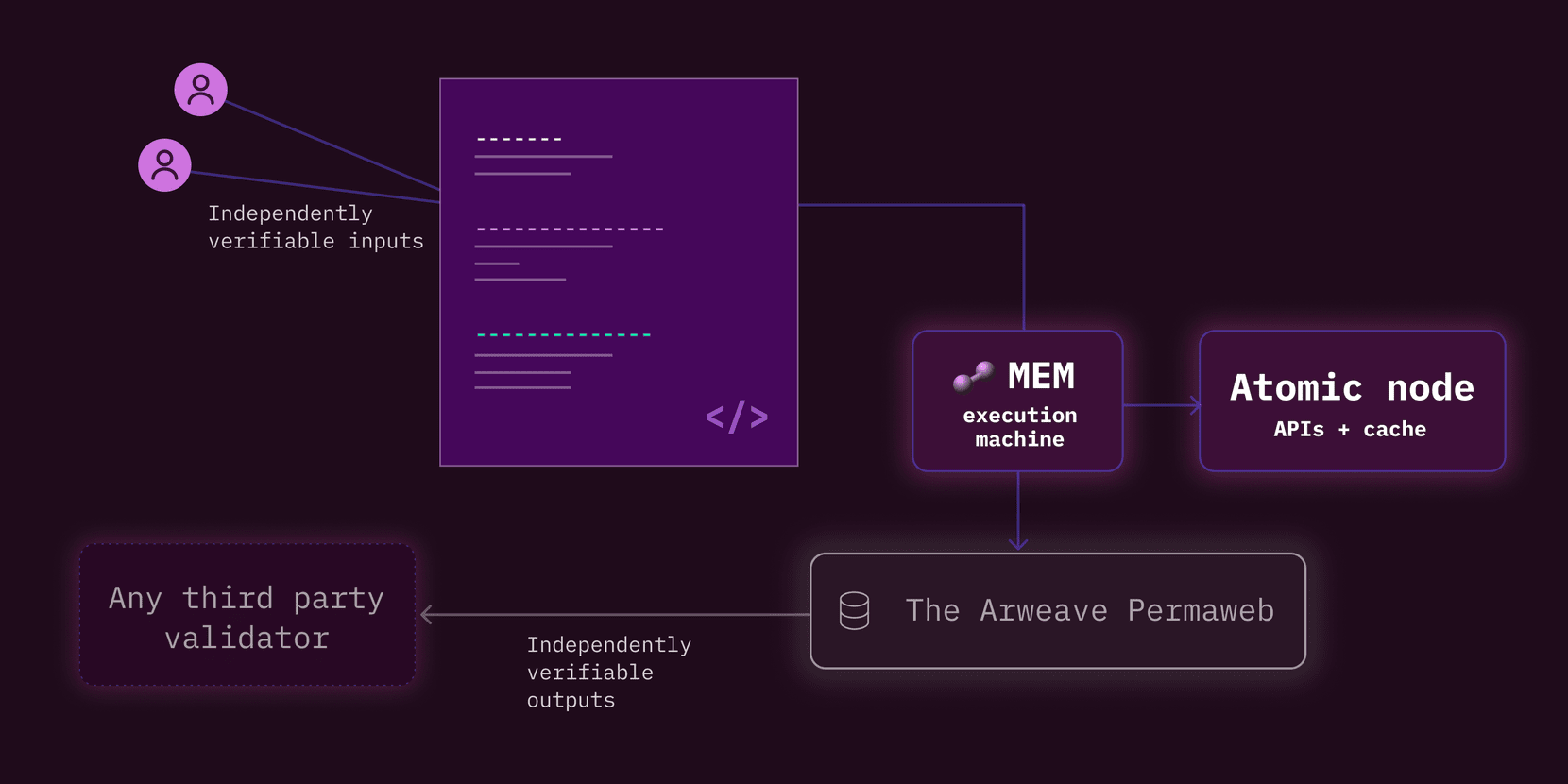
VACP Visualization
1. Data calculation rules and initial status upload:
A set of rules (smart contract/serverless function code) and initial state are uploaded to the Data Availability (DA) layer.
The initial state records all state changes over time.
2. Trusted third party (TTP) for user interaction processing, also known as atomic node:
A trusted third party (TTP) can be a highly scalable centralized node responsible for managing user interactions within the system.
The credibility of TTP relies on trust, which is established based on the fidelity (data authenticity and validity) of the data uploaded to the DA layer.
The trustworthiness of a TTP depends on its ability to pass verifiable computational checks by end users, ensuring the integrity and accuracy of its actions.
The TTP handles tasks such as receiving user transactions, evaluating new states, and maintaining data caches.
Essentially, VACP leverages a combination of rules and data uploaded on the DA layer and trusted entities (TTPs) to enable verifiable computation while maintaining a level of scalability and trust in the operation of the system.
MEM is a VACP implementation
The Molecular Executive Machine (MEM) is a legitimate implementation of the Verifiable Atomic Computation Paradigm (VACP) because it adheres to the basic paradigm requirements:
Atomicity: MEM operates as a single node (Trusted Third Party - TTP) and is able to run an efficient and scalable web2.5 network.
Verifiable Computation: Within the MEM framework, atomic nodes are constantly subject to rigorous honesty checks performed by end users or any interested parties. Every operation performed by the node can be replicated and verified, ensuring transparency and trust within the system.
In MEM, smart contracts and interactions are located in the same DA layer, facilitating final state verification through lazy evaluation and verifiable computation principles, in line with VACP.
What happens if an Atom node turns into a malicious actor?
The VACP system has protection mechanisms in place if an Atomic Node is identified as a malicious actor. At any given moment, if an Atomic Node is determined to be behaving dishonestly, any interested party can access the immutable VACP interactions stored in the Data Availability (DA) layer. They can then perform lazy evaluation and reconstruct the transaction history until the last honest state is reached.
The system can then initiate a "hard fork" of the network from the block height corresponding to the last known honest state, effectively ignoring any fraudulent actions taken by malicious atomic nodes. This approach allows the network to continue operating from a trusted point while isolating and mitigating the impact of the dishonest actor's actions, thereby ensuring the integrity and trustworthiness of the network.
What is the difference between VACP and MEM in the field of smart contracts?
MEM adheres to the VACP principles and redefines the data-driven smart contract landscape by providing enhanced scalability, better user and developer experience, diverse data sources, protocol evolution, atomic node efficiency, optimal Arweave DA layer utilization, and affordability. This comprehensive approach makes MEM a pioneer in the field:
Scalability and Throughput: MEM achieves superior scalability and transaction processing capabilities, surpassing other platforms in terms of transactions per second (TPS) and transaction finality and latency. This enables the network to handle more interactions.
User Experience (UX) and Developer Experience (DX): The implementation of VACP will result in a more user-friendly and developer-friendly ecosystem in MEM, making it more accessible and productive for both users and developers. This competitive advantage promotes adoption and innovation.
Data Source: While MEM relies on a single data source at the DA layer (Arweave L2), it leverages that data source efficiently to create a faster and more secure sequencer for data-driven smart contracts.
SmartWeave Protocol Evolution: MEM implements 3EM using an improved SmartWeave protocol, ensuring it is at the forefront of protocol advancements, incorporating the latest innovations in data-driven contract technology.
Atomic Node Concept: MEM adopts the atomic node concept, providing a lightweight and highly scalable approach that outperforms competitors in terms of efficiency and responsiveness.
Leverage of the Arweave DA layer: MEM avoids the limitations associated with Arweave tags by using data transactions as interaction placeholders. This innovation allows enterprise-scale contract data computation requests, unlocking new possibilities for data-driven smart contracts.
Web2.5 Optimization: MEM focuses on delivering Web2.5 UX and DX to meet the needs of both enterprise and consumer segments, creating opportunities for growth and expansion.
Low-cost and efficient network setup: For less than $100 per month, anyone can deploy their own web2.5 data computation network using the open source MEM codebase. This cost-effective approach leverages the right combination of Web2 components and software to enable MEM to achieve rapid scalability, eliminate the need for traditional cache designs, and shift responsibility to contract deployers.
UI-driven data proof based on VACP protocol
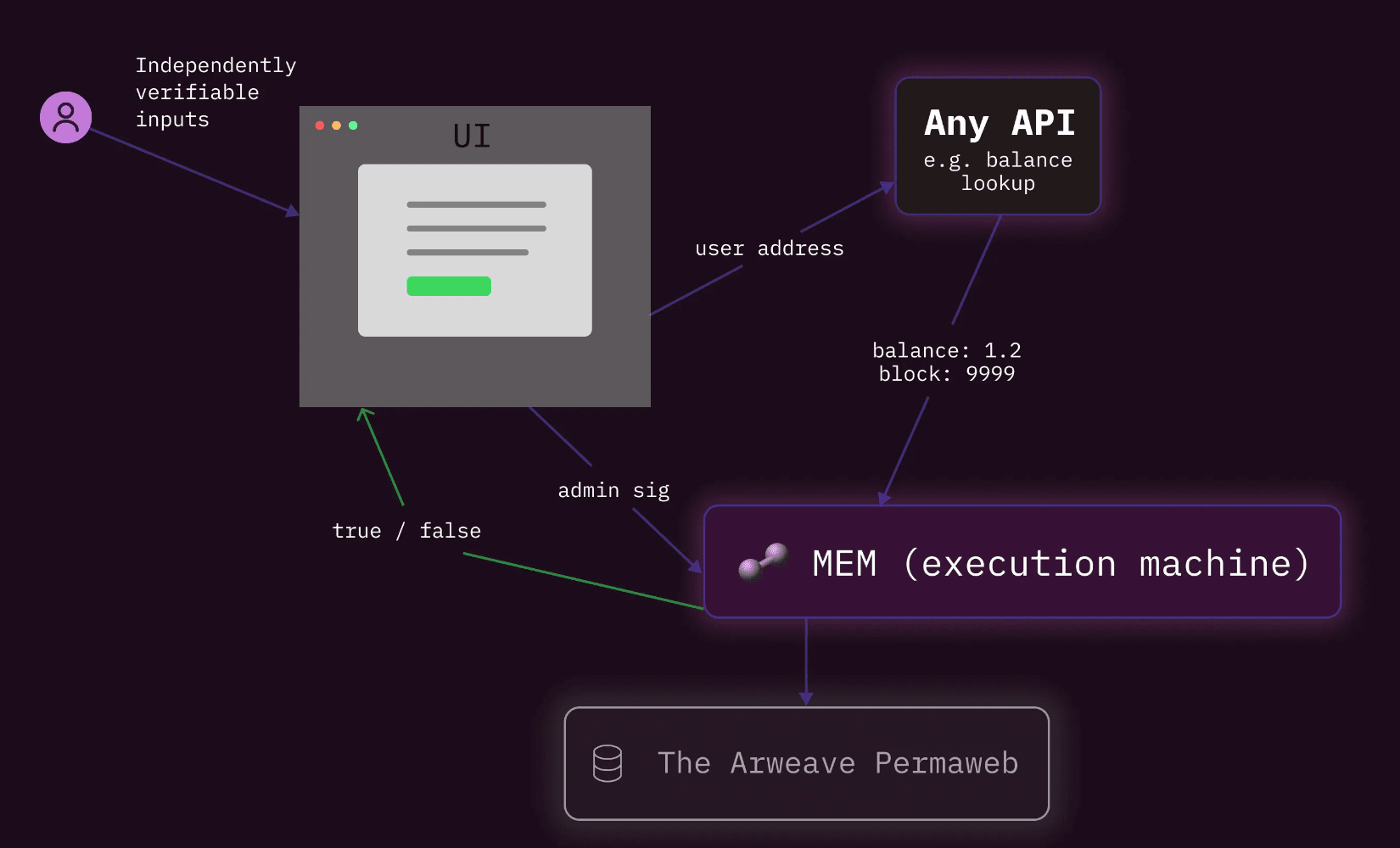
ACP with MEM and on-chain data Token-Gating example
(Note: Token-Gating: is a security mechanism that limits users or applications from accessing and using certain specific content or services by assigning access tokens to different resources or functions. This mechanism can be used to protect personal data, sensitive information, or digital assets from unauthorized access and use.)
Consider a scenario where an application user interface (UI) can provide proofs about data it obtains and assumes to be authentic (e.g. checking the balance of a connected wallet for token gating purposes) based on information retrieved from the Ethereum network. This proof should include the necessary metadata:
FE requests Ethereum blocks for Externally Owned Account (EOA) balances.
Token contract address.
Timestamp proofs when data requests are made on the persistent data availability (DA) layer using a molecular execution machine (MEM).
Once this proof metadata is collected, it can be submitted to the MEM contract, which will store it as a permanent proof. Any user can verify the validity of this proof and the proof by implementing the Verifiable Atomic Computation Paradigm (VACP) principles.
Summarize
In summary, VACP redefines the concept of Web2.5, providing a model that combines trust, scalability, cost efficiency, user experience, data integrity, interoperability, and innovation, ultimately providing a practical and scalable framework that bridges the gap between the Web2 and Web3 paradigms.


