
“Terrorists use obscure cryptographic tokens to circumvent traditional screening and raise funds.”

Terrorist organizations are increasingly inclined to use blockchain technology to raise funds and evade supervision, and the proportion of their financing through cryptocurrency may be as high as 20%.
Mainstream terrorist groups such as al-Qaeda, Hamas’ al-Qassam, and the Islamic State are using cryptoassets to achieve a variety of goals, such as sanctions evasion, cybercrime, extortion, and fundraising.
While these organizations no longer primarily use Bitcoin, stablecoins such as Tether (USDT) are increasingly gaining traction.
Therefore, law enforcement agencies must increase their ability to track multiple cryptoassets. In addition, public fundraising, mining and DeFi investment are also the main ways for terrorists to raise funds in the encryption field.
Terrorist groups are increasingly engaging with the crypto space and using developments in blockchain technology to raise funds and evade detection by authorities. The United Nations predicts that cryptocurrencies may account for 20% of terrorist financing.
1. "Public Fundraising"
Cryptocurrency-based terrorist financing often solicits donations through social media or private networks, and publishes dedicated donation wallet addresses.
Numerous public fundraising activities have raised millions of dollars for terrorist organizations, such as the Islamic State and Al Qaeda, which have raised more than $3 million.
Additionally, cryptocurrency usage has been linked to geopolitical events, such as Palestinian Islamic Jihad (PIJ) wallets being linked to the conflict between Israel and Palestine.
While wallet seizures have had an impact on fundraising, some organizations have adapted their strategies and chosen to accept donations in privacy-friendly cryptocurrencies to stay afloat.
2. "Fraud and Darknet Activities"
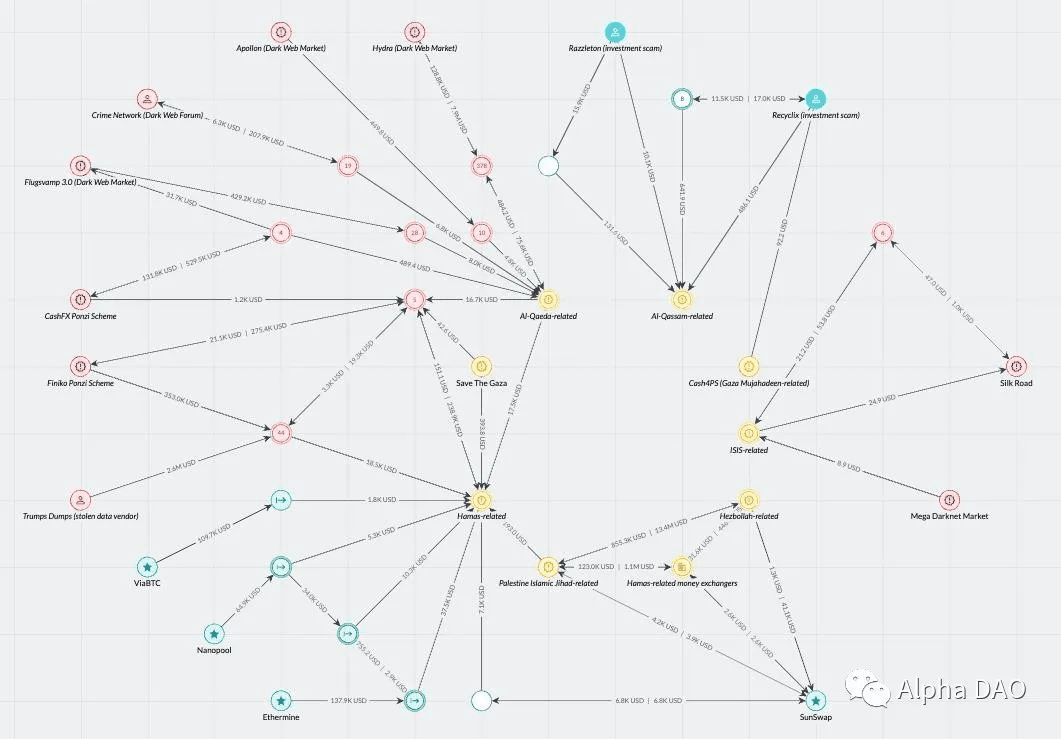
Using our forensic investigation tool, Elliptic Investigator, we were able to demonstrate the movement of funds to and from a number of wallets and various sources associated with several major terrorist groups. These sources include stolen credit card providers, darknet markets, Ponzi schemes, and cryptocurrency investment scams.
This activity reflects terrorist links to other ways of making money and acquiring weapons. Links between terrorist financing and credit card fraud have been revealed in a number of seizures and criminal cases in the US and UK.
3. "DeFi Trading and Investment"
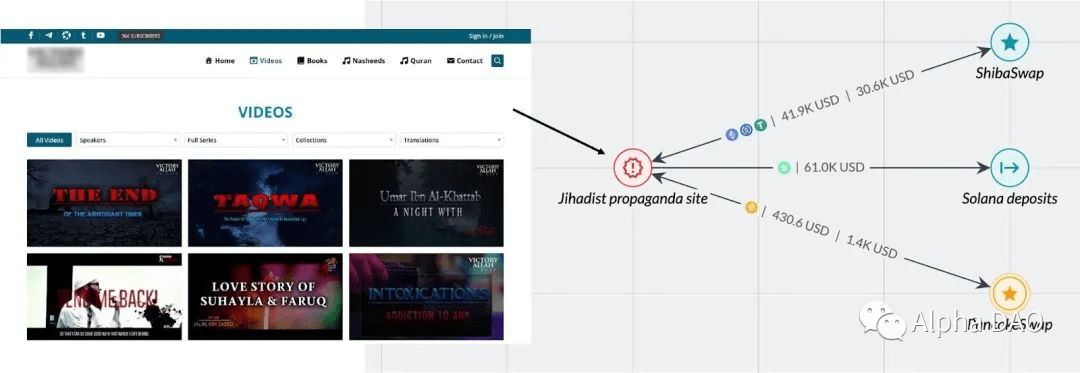
Although terrorist exploitation of DeFi is rarely observed, one particular case study (involving the use of the technology by one of the most successful terrorist entities in the cryptocurrency space) highlights this risk and provides insight into how DeFi technology can be exploited .
One particular website we decided to anonymize accepts funds from addresses closely associated with DeFi protocols, suggesting that the majority of the incoming assets are not donations but earnings from investments made by the site’s administrators.
In fact, more than 21% of their funds on the Ethereum and Binance Smart Chain (BSC) blockchains come from decentralized exchanges, with accounts containing a variety of stablecoins and DeFi-specific assets.
Overall, the site saw over $300,000 in crypto assets, $51,000 of which came from Solana (SOL). The website’s wallet balance shows a $10,000 profit on Solana’s investment alone. Proceeds from transactions are both generated from various centralized exchanges and can be redeemed into stablecoins, including over $250,000 in USD Coin (USDC).
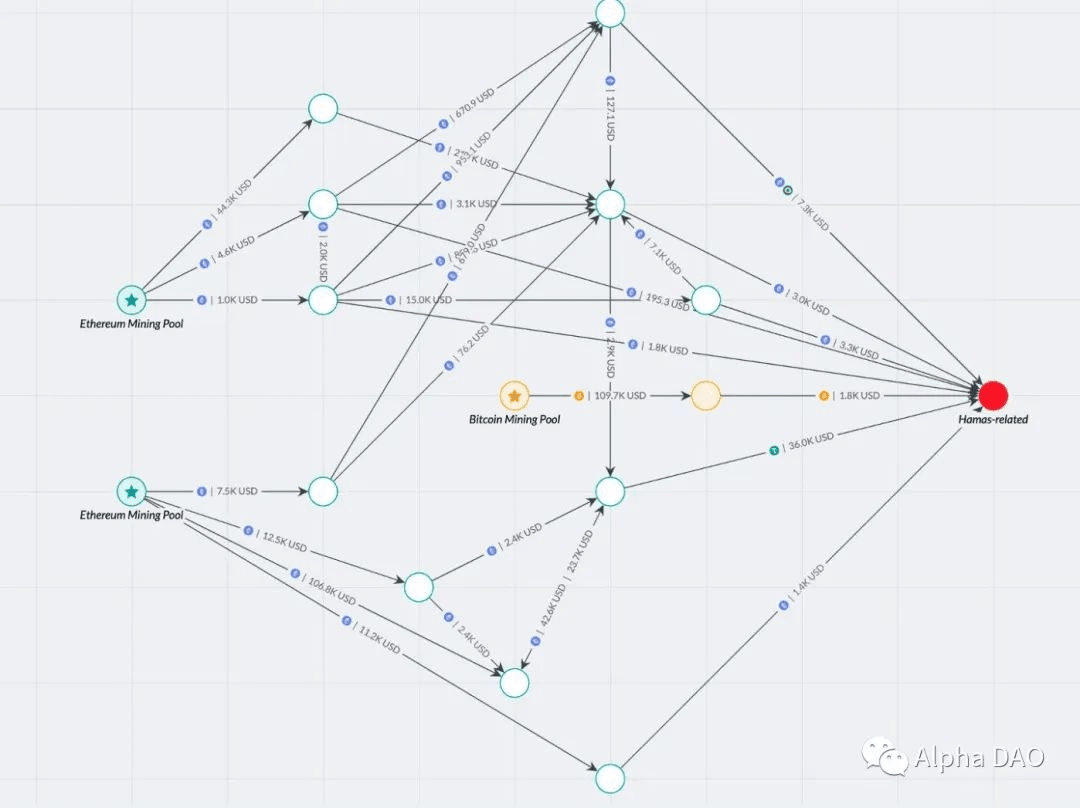
4. "Cryptocurrency Mining"
Cryptocurrency mining is being used by terrorist groups for a variety of purposes, such as evading sanctions and financing terrorism.
Iran, which funds groups involved in terrorism such as Hezbollah and its Islamic Revolutionary Guard Corps (IRGC), has turned to cryptocurrency mining to bypass sanctions.
Meanwhile, blockchain analysis has found that other terrorist groups, such as Al Qaeda and Qassam, are also involved in mining activities. The Islamic State has even shared cryptocurrency mining guides and links to preferred mining pools.
Conclusion
Our research can help law enforcement investigators identify and counter the latest techniques used by terrorist groups to evade detection and raise funds.
Additionally, as terrorists are experimenting with new and unknown crypto tokens, terrorist financing is more likely to be missed by traditional screening programs that only cover traditional assets. Extremist groups continue to find new ways to monetize or disguise funds supporting terrorist activities through chain/asset hopping.
✏️Disclaimer: This article is for reference only, DYOR
「Alpha DAO」
A Web3 Chinese community that does not serve as cannon fodder;
Track the latest hot spots and interpret the industry track;
Leverage the strength of the wind and share the prosperity together.


