Author: Jagjit Singh, Cointelegraph; Translated by: Songxue, Golden Finance
1. Understanding Known Plaintext Attacks
A known plaintext attack (KPA) occurs when a hacker uses a well-known pair of unencrypted and encrypted material to determine an algorithm or encryption key.
In a known plaintext attack, the attacker has access to the encrypted form of the data (the ciphertext) and its corresponding plaintext copy (the unencrypted form) of the original data. The attacker attempts to determine the encryption key or algorithm by examining the relationship between the plaintext and the ciphertext.
For example, if "CRYPTO" is encoded as "XUZZA," then knowing this pair could enable an attacker to decode other parts of the message that were also encrypted with the same substitution key. This shows that with certain encryption algorithms, even a small amount of knowledge can enable more extensive decryption.
This attack exploits flaws in cryptography that allow identification of patterns or connections between plaintext and ciphertext. If not properly prevented, known-plaintext attacks can compromise the security of encryption systems.
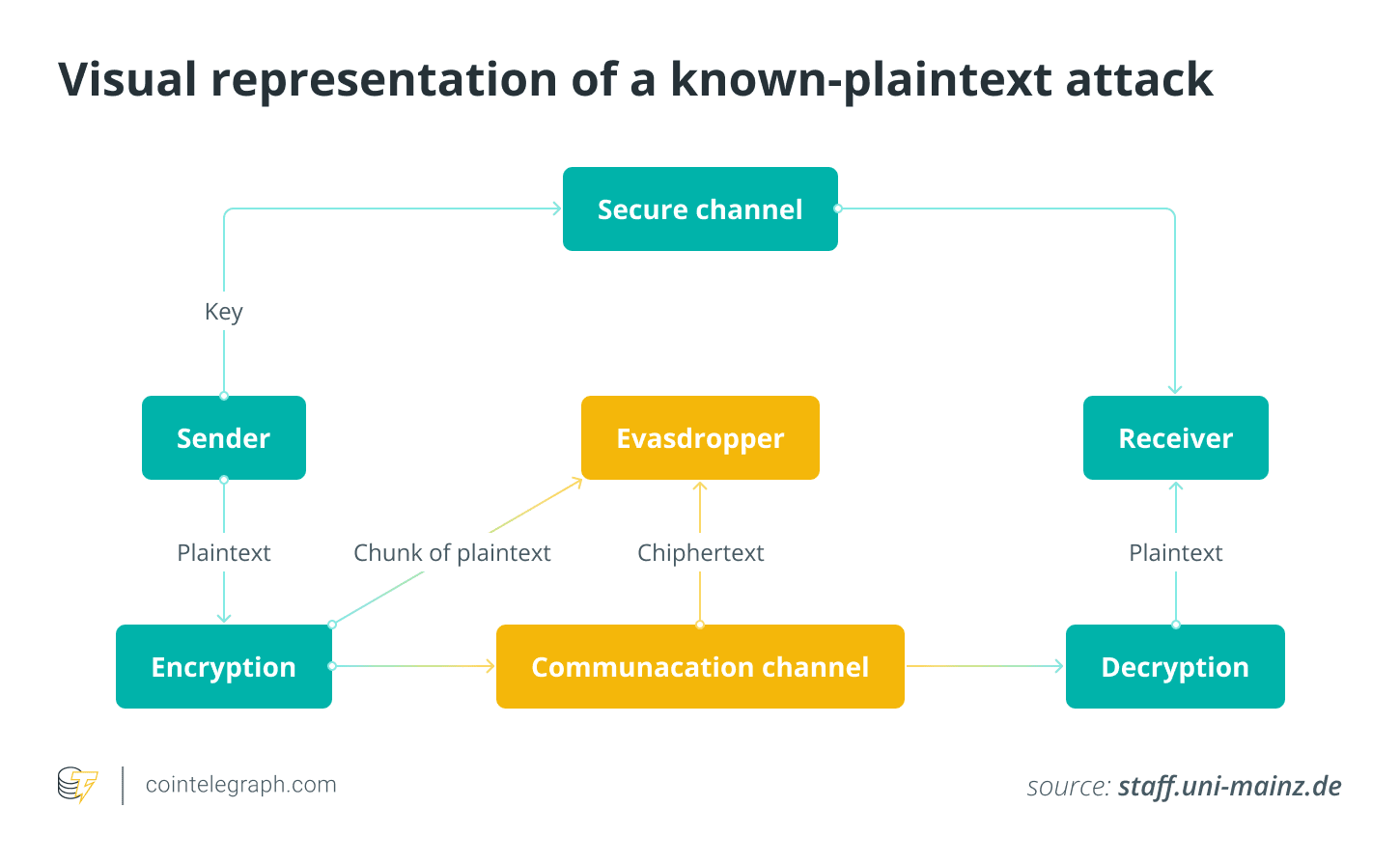
Two common methods of using plaintext and its corresponding encrypted form to reveal encryption keys include frequency analysis and pattern matching. Frequency analysis methods use simple encryption methods and one-to-one letter or symbol substitution. An attacker can find out the key or unlock the rest of the communication by comparing the frequency of occurrence of specific letters or patterns in known plaintext and related ciphertext.
When the same plaintext produces the same ciphertext in a pattern matching method, attackers can spot a trend. They can identify the encryption algorithm and decrypt the entire message by identifying patterns in the encrypted text and comparing it to known patterns in the plaintext.
2. How is a known plaintext attack performed?
In a KPA, an attacker can learn important details about an encryption method by analyzing how a specific block of plaintext is converted into ciphertext using the same encryption key, or algorithm.
The attack involves the following steps:
Collect known pairs
The attacker accumulates the original plaintext and the associated encrypted ciphertext obtained through various techniques such as intercepted communications or data exfiltration.
Analysis Mode
When plaintext is encrypted to create ciphertext, attackers compare the patterns, modifications, and transformations that occur. To understand the operation of the encryption process, they search for regular relationships between known plaintext and ciphertext.
Derived key or algorithm
Attackers try to determine key cryptographic elements, such as encryption keys, algorithms, or other process parameters based on the patterns they notice. Thanks to this deduction, they can independently replicate the encryption process.
Decrypting other data
An attacker can use the derived key or algorithm to decrypt other cryptographic material that uses the same encryption algorithm. This process may reveal confidential information or compromise the security of the encryption system.
3. Chosen Plaintext Attack and Known Plaintext Attack
A chosen plaintext attack involves the adversary choosing a plaintext and analyzing the corresponding ciphertext, whereas a known plaintext attack occurs when the attacker has partial knowledge of the plaintext.
Understanding the difference between these two types of cryptojacking attacks is critical to an effective cryptojacking defense strategy.
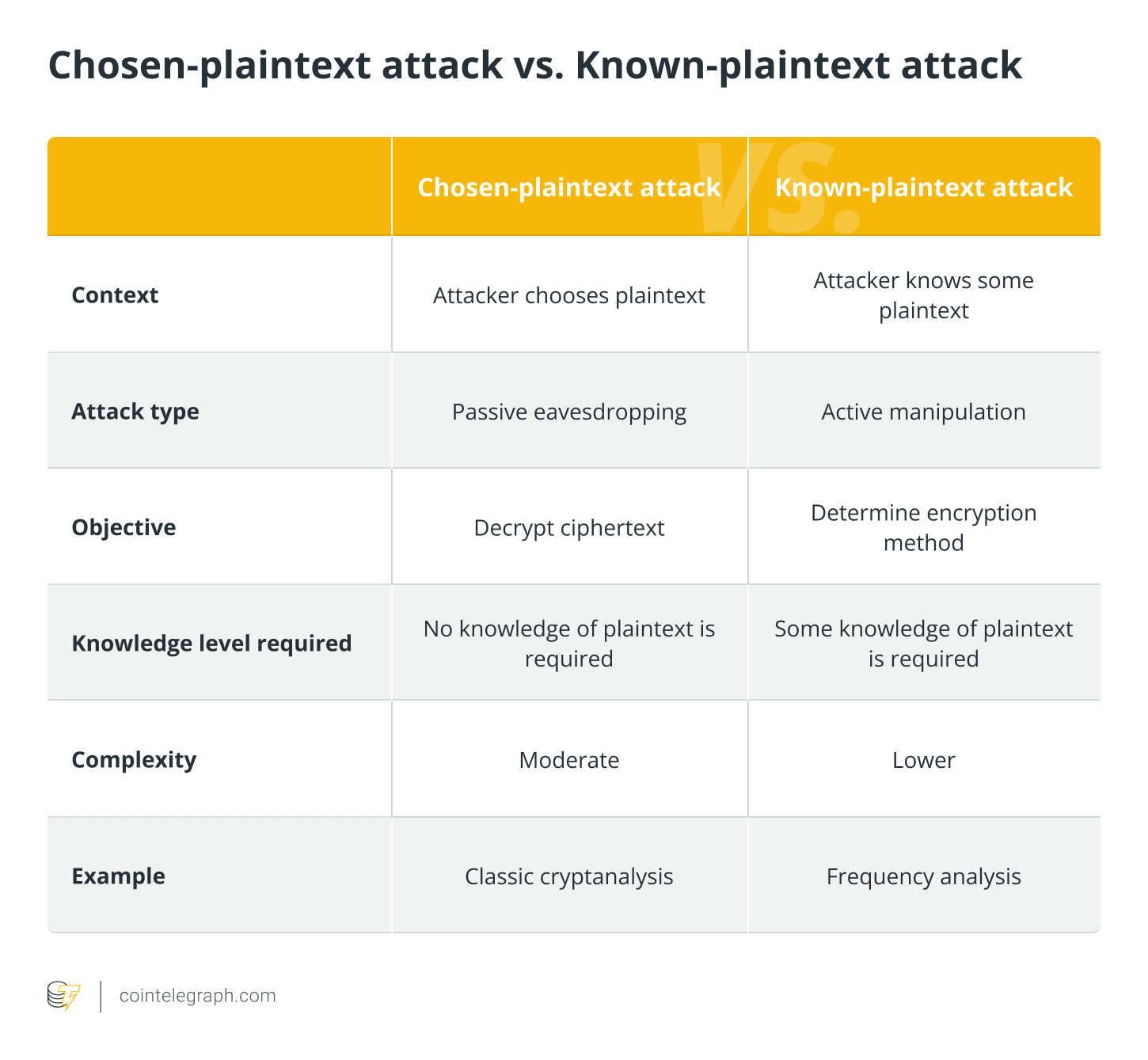
Frequency analysis focuses on examining the occurrence of letters or symbols to determine the encryption algorithm, which is different from classical cryptanalysis, which examines ciphertext for patterns and flaws.
4. How to prevent known plaintext attacks?
To protect against known-plaintext attacks, employ strong encryption algorithms, securely manage encryption keys, use unique keys for each session, and add randomness to the encryption process to increase protection against attacks.
Choose an encryption algorithm that is resistant to known-plaintext attacks by using strong cryptographic techniques. Modern encryption algorithms such as the Advanced Encryption Standard (AES) protect against such attacks by preventing patterns in the plaintext from being correlated with patterns in the ciphertext. AES is a widely used symmetric encryption algorithm known for its security and efficiency.
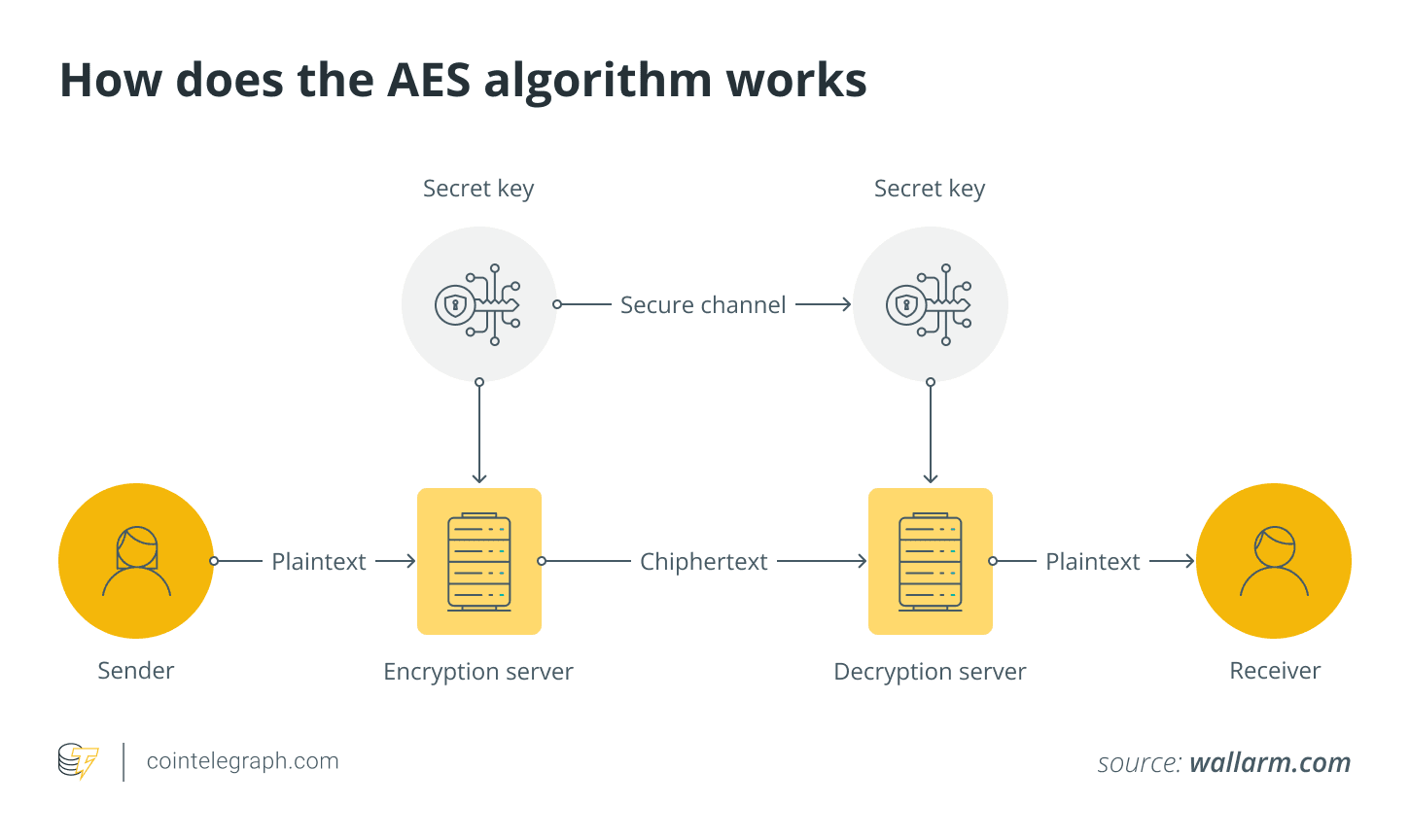
Manage encryption keys securely to avoid unauthorized access. Use a secure key repository, rotate keys frequently, and use strong key generation techniques. Also, avoid encrypting discrete, predictable blocks of data. To prevent attackers from using known pairs, encrypt the entire message or file.
Additionally, use different keys for different sessions and tasks. Since each session will use a different encryption key, the impact of known plaintext attacks is reduced. Also, maintain the latest versions of your system, libraries, and encryption software. Security fixes that correct vulnerabilities are frequently included in updates.
Before encrypting the plaintext of your data, add a cryptographic salt (a random value) to it. This makes each encryption unique, even if the same plaintext is encrypted multiple times. Also, avoid encryption methods that are known to be vulnerable to known-plaintext attacks. That said, do proper due diligence when choosing an encryption algorithm.
