To protect your Binance account and assets, always pay attention to the URL before attempting to log in. When using the official Binance website, you can confirm the URL as shown below for your peace of mind:
Official Binance website: https://www.binance.com/en-jp
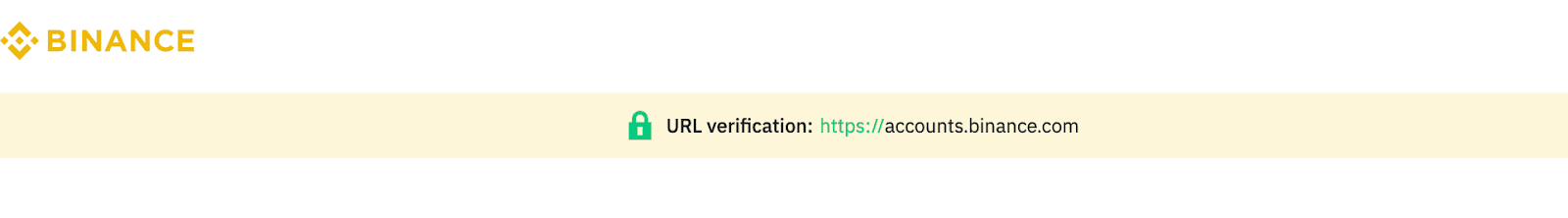
Please always make sure that the URL domain name is “binance.com” and the URL begins with “https://”.
Beware of phishing websites on search engine results, browser plugins or extensions, third-party applications, and emails. These fake sites are malicious attempts to trick you into exposing your personal information, such as Binance login credentials. These fake sites are malicious(2FA) codes and other sensitive information.
By using the official Binance Verify feature, you can easily verify whether a website URL or email address truly belongs to Binance.
Below are some examples of fake Binance websites:
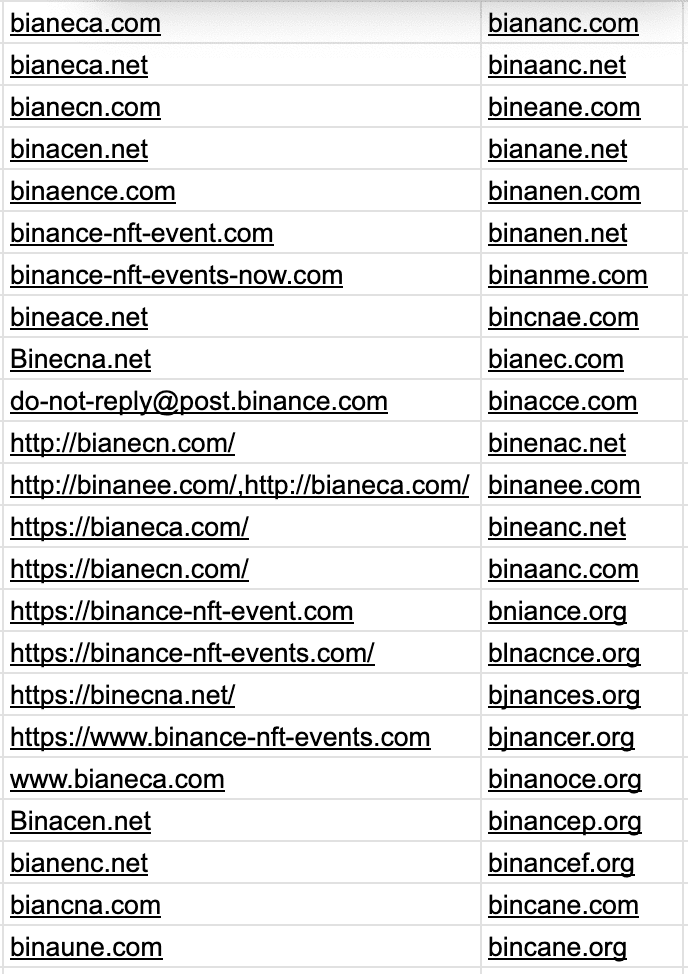
When logging in, please pay attention to the following points:
To protect your safety from cyberattacks and help you avoid phishing sites, we highly recommend installing the official Netcraft anti-phishing browser plugin.
You can download the plugin from the official site: https://toolbar.netcraft.com/
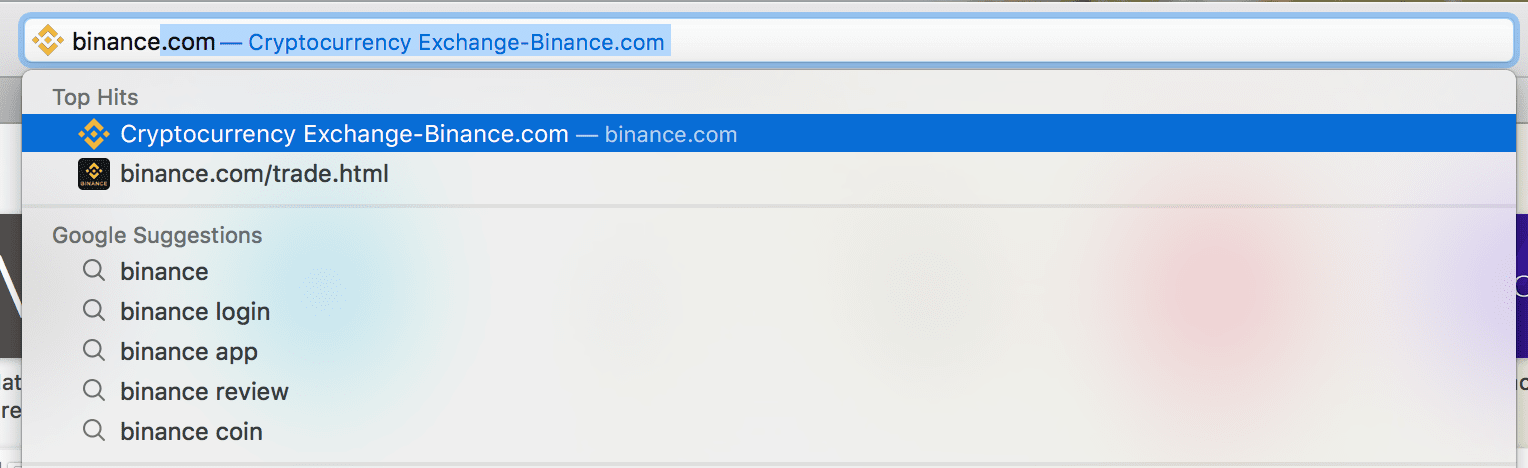
There have been reports of browser plugins and extensions that redirect users to fake websites when searching online. Below the example case to help you understand this issue better.
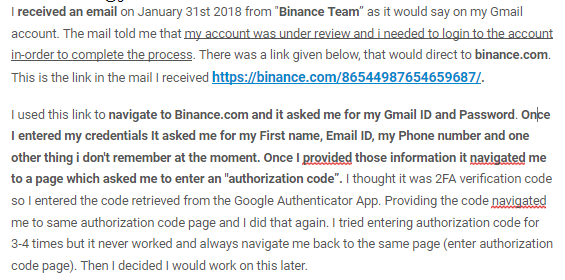
Here is an example of a dangerous email containing links to phishing sites.
This user has managed their portfolios using third-party apps or have downloaded unauthorized apps from unofficial app stores.
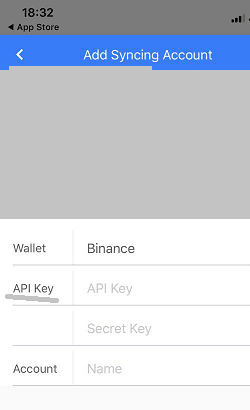
Phishing sites cleverly steal sensitive information like passwords and two-factor authentication recovery codes. With this information, hackers can exploit your API access to make unauthorized withdrawals and place suspicious trades.
Analysis of the access logs from affected users confirmed that they accessed the phishing sites through search engines.
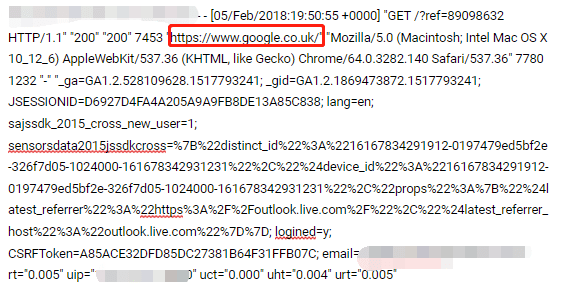
Example of server logs from the incident:
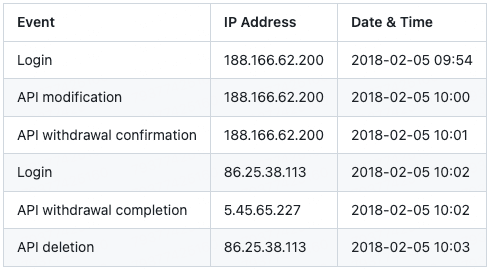
Users who fell victim to the phishing attack shared the following details regarding the circumstances of the incident:
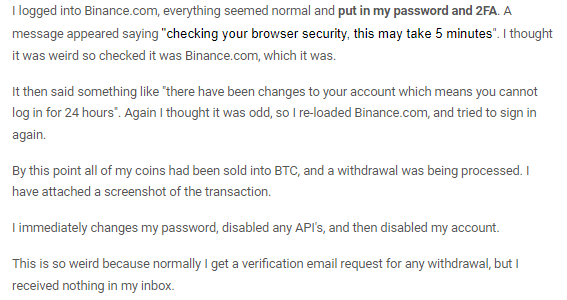
For more details and tips, please refer to: