In fact, in most asset theft incidents, the last security door (signature authorization) is guarded by the user himself. If the user is careful and understands the content of the signature, he will most likely be able to avoid many risks.
So what are the types of wallet signatures? How to identify suspicious transactions? Next, the author will briefly introduce this aspect.
The difference between signature and authorization
First of all, it is necessary to popularize the difference between signature and authorization.
Simply put, a user signature is just like a company chairman signing a document. It is a method of authentication and permission. All interactions, whether it is ordinary identity authentication, transfer, or operations in Dapp, ultimately require our signature operation to proceed. In the actual use of the wallet, as long as the authentication interface (including Sign, Confirm, etc.) pops up, the application is seeking your signature. One authentication is equivalent to a signature.
Authorization (including Approve, Permit, etc.) is to grant certain permissions to the application (for example, transfers below 0.1 ETH can be performed on behalf of the user), which is a subset of signatures. In the actual use of the wallet, the signature may bring some authorization, but the authorization must be signed by the user. It is worth noting that authorization is intended to improve user experience, but when authorizing, you must also carefully screen the authorized objects and content to prevent asset theft.
Especially for hair-pulling users, in order to do interactive tasks, the wallet may have accumulated various website authorizations. The safe suggestion is to check the wallet authorization regularly and cancel the authorization of some suspicious or infrequently used websites, otherwise the hard-working hair-raising The boutique number may be a wedding dress made for someone else.
Revoke is currently the most commonly used website to view and cancel wallet authorization. The link is as follows:
https://revoke.cash
 不同的签名类型
不同的签名类型
In Ethereum, there are three main signature methods: Personal_Sign, EIP712 Sign (eth_signTypedData), and Eth_Sign.
Personal_Sign
Personal_Sign is the most common signature method and is often used for identity verification and website and Dapp login operations.
In the figure below, the Personal_Sign used when logging in to Opensea is taken as an example. Let’s introduce the parts and precautions of this signature one by one:
1. The top is the user’s account and balance, there is nothing much to say;
2. Below is the domain name of Opensea. Many users sometimes ignore this information, but it is worth checking because some phishing websites will forge the same signature under their own domain name to trick users into being fooled, so whether it is in the browser Whether you log in to the Dapp or perform subsequent interactive signatures in the Dapp, you need to check whether the domain name is correct;
3. At the bottom is the message. There are 6 pieces of content in total, including the ones marked in the picture below: (1) Welcome message (2) Disclaimer contract (3) Reminder that this signature will not cost Gas (4) Reminder that this signature is valid The wallet address (6) signed for 24h (5) proves that the signature is a unique nonce.

However, not all Personal_Sign messages of applications can achieve the level of "what you see is what you sign" like Opensea. Some application graphs are easy to write and are not as complete as Opensea, and some simply directly present a string that is unreadable by users. (commonly known as "blind signing"), even if there are no security issues, it can reflect that this kind of project does not pay attention to user experience.

EIP712 Sign(eth_signTypedData)
EIP712 Sign is a more readable signature method, so it is often used for signatures related to contract interactions, such as buying and selling NFTs, swap interactions, governance voting, etc.
As shown below, the top information is similar to Personal_Sign, including account, balance and domain name. The difference is that the bottom message is not only readable but also displayed according to different types (From, Wallet, To, Amount, etc.), which allows users to more It is good to check whether the content to be signed is correct.

However, this does not mean that EIP712 Sign is absolutely safe. If the user never reads the content when signing, it will be useless no matter how detailed it is. Just like in this Galxe attack, the transaction content was clearly written in the signature (although it was not EIP712 Sign), but some users were still affected.
Eth_Sign
Eth_Sign is a signature method provided by MetaMask very early on. It is recognized as a very dangerous signature method and is commonly used by scams. Because Eth_Sign is a complete "blind signature", the string presented in the bottom message is unreadable. The user has no idea what they are signing. It may be a website login request or an authorization, or it may be a transaction that transfers all your assets.
Therefore, when encountering Eth_Sign's signature MetaMask, a red warning (as shown below) will generally be raised to remind users not to enter the scam, but it does not rule out the possibility of no warning. In short, when encountering this kind of "blind signature", as a user, it is the safest way not to sign at all.

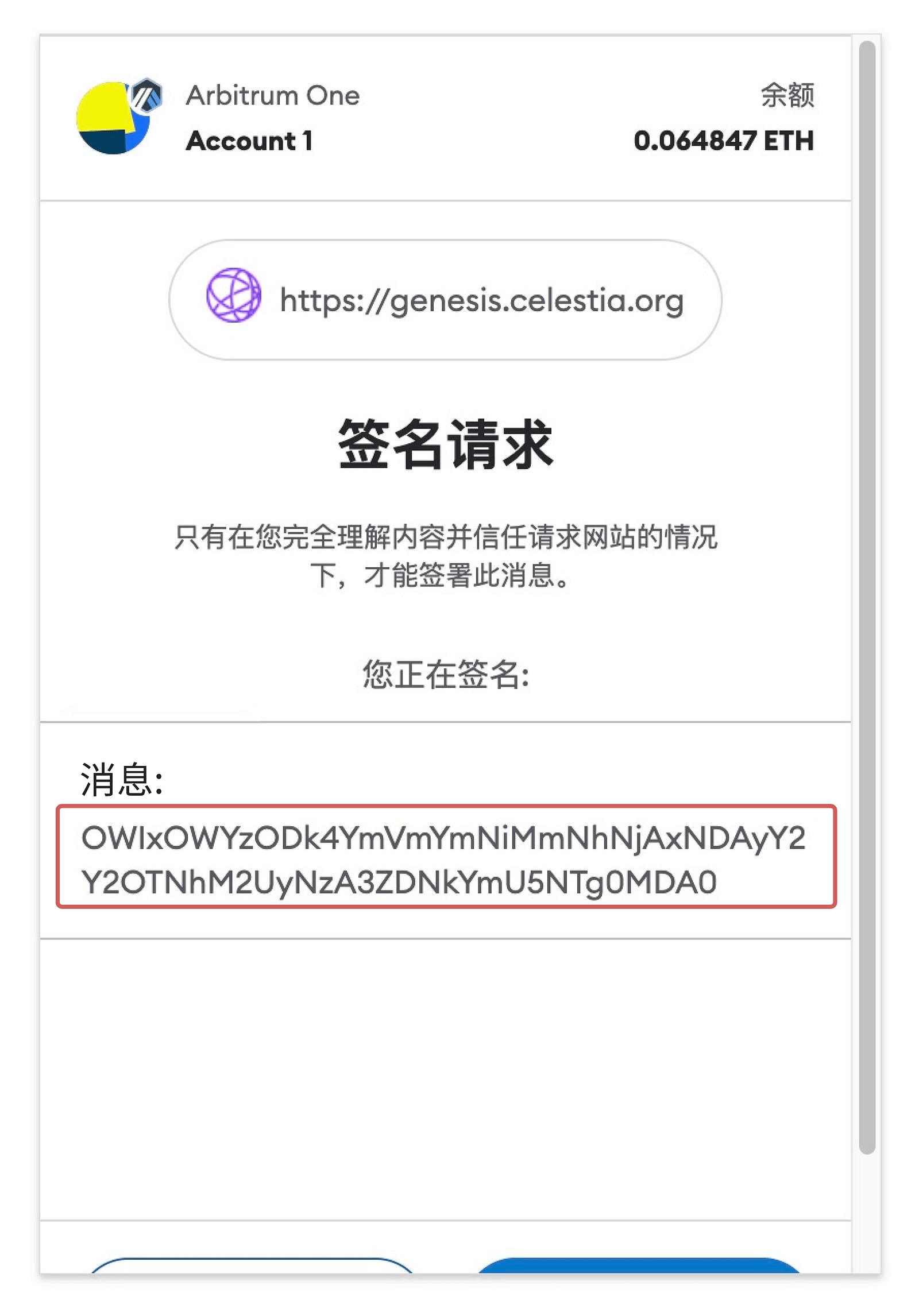
Of course, for "blind signature" content, an identification trick is that if the string starts with "0x", then there is a high probability that the signature involves a transaction; if it does not start with "0x", it may be identity authentication or authorization. Signature (pictured below).
 总结
总结
Not only do we need to understand what an attack is, but more importantly, we need to sound the alarm for ourselves.
The above is just a brief introduction to several signature methods and things you need to pay attention to when signing. This may not help you avoid all phishing attacks, because hackers' phishing and attack methods are constantly updated. But in any case, the only thing to keep in mind is that you must guard the last security door of "signature". In real interactions, no matter how small the signature is or how well-known the website requires authorization, you need to be careful and carefully verify the content to be signed. .
