Audit sign-off week is when DuskEVM stops being a vision and turns into a risk memo.
A team I know had the contracts done, audits paid, playbooks written. Then the migration question landed in the worst form... "What changes that forces us to re approve?" Not throughput. Not roadmap. Execution semantics, tooling assumptions the stuff ops and security teams already bled for though.
And audit week is also when Dusk Moonlight's "confidential by default" stops being a design choice and start breaking monitoring assumptions.
Dusk Ethereum virtual machine, DuskEVM is what keeps that re approval blast radius from expanding. Solidity stays Solidity. Deployment doesn't turn into a re education program. Wallets keep signing the way the runbooks expect. The part procurement actually signs is boring: you can move without rewriting your week.
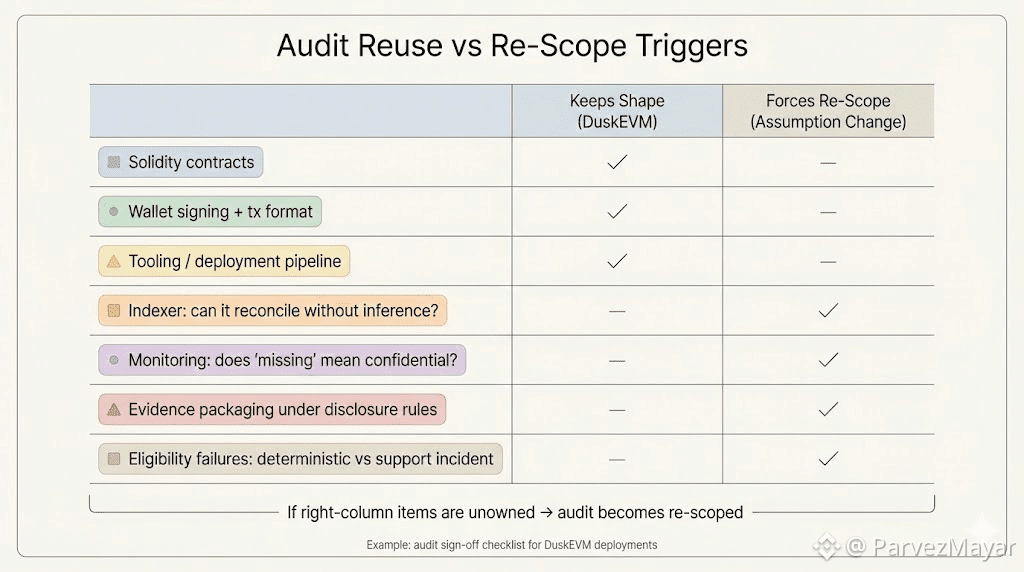
But portability only counts when pressure hits.
The minute execution semantics drift, the audit stops being 'reused' and becomes "re-scoped', You re-open threat models. You re run invariants. You re-argue findings that were already closed. That is not a technical problem. That's a calendar problem, and calendars eliminate migrations faster than bugs do.
DuskEVM is the difference between "scope stays intact" and "scope reopens"'. The regulated machinery lives below it: settlement proofs, disclosure boundaries, eligibility checks that fail deterministically instead of being "handled later." Same contracts. Stricter rails. Different places to get surprised.
Dusk stops being "just another EVM" in the boring places.
Moonlight and Phoenix aren't marketing lanes as Dusk seprate transaction models but... They change what your app can see and what your observability stack can safely assume. If you've built dashboards that rely on reading everything, Moonlight breaks that assumption. If you've built compliance flows that rely on someone emailing a confirmation, Phoenix breaks that too, because the boundary is rule-bound, not operator-bound. Same contract, different environment, different failure modes.
Teams do not hesitate because they're scared of new RPC endpoints. They hesitate because of the production checklist.
Will the indexer still reconcile state without inventing stories?
Will monitoring stay truthful when some flows are confidential by default?
When an eligibility condition fails, does it fail cleanly at the call site or become a support incident?
And the one that shows up on a Thursday 6pm call, right before someone tries to close the doc: when evidence packaging and review gates stack up, do we still have a usable settlement window, or do we start telling people "soon"?
That is the adoption mechanics honestly. Not incentives. Whether the first messy day turns into a post-mortem.
DuskEVM usually shows up late in the conversation, after someone has already bought the privacy/compliance thesis and then asks the only question that matters in a builder channel: "Are we re-auditing everything?"
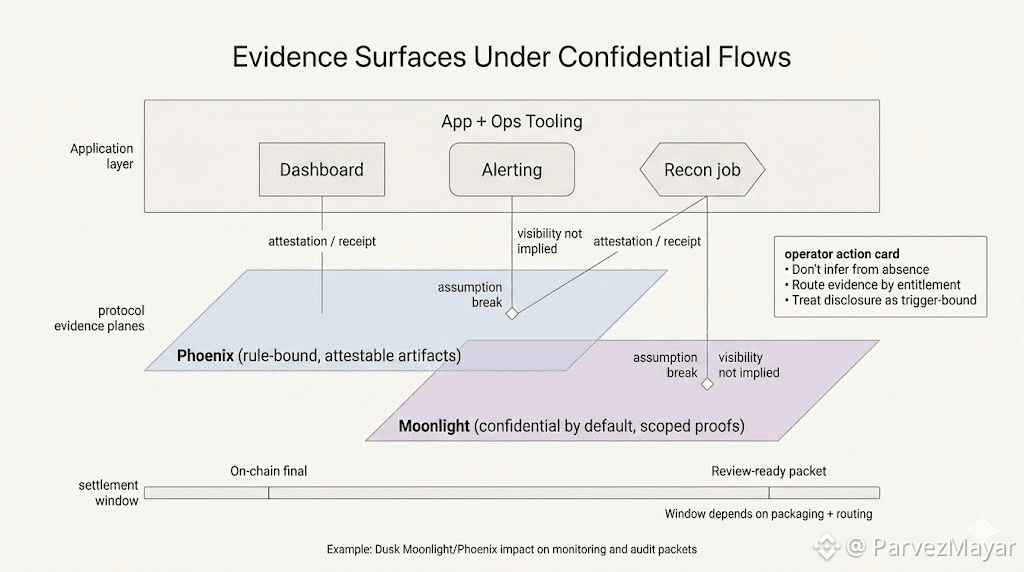
If the honest answer is "your contracts mostly keep their shape, but your ops assumptions need to respect Moonlight/Phoenix boundaries," a migration review gets scheduled. If the answer is "new VM, new mental model, new audit scope," it dies quietly.
The hard part isn't shipping the first deployment.
It's the first week you get a Moonlight-heavy workload, a reporting trigger is waiting and somebody asks for a yes/no decision you cant soften... without requesting a scope expansion you don't have authority to approve.


