Executive Summary


Network represents a vertically integrated approach to decentralized verifiable compute, combining custom hardware acceleration with blockchain coordination to address the structural problems of ZK proof centralization and AI compute trust deficits. The protocol has transitioned to early mainnet (December 2025) with demonstrated technical capability (7M+ proofs generated) and substantial community interest (23,000+ verifier applications). At current valuation ($64.3M market cap, $400M FDV), Cysic sits at an inflection point where execution risk remains high but differentiation is clear through hardware integration.
Key Investment Thesis: Cysic's value proposition hinges on becoming the default verifiable compute layer for ZK rollups and AI protocols by solving the trilemma of decentralization, performance, and cost through specialized hardware and cryptographic verification. Success requires overcoming capital-intensive hardware deployment, proving economic sustainability beyond subsidized emissions, and capturing demand from both crypto-native and traditional compute markets.
1. Project Overview
Cysic Network operates in the verifiable compute infrastructure sector, specifically targeting ZK proof generation and decentralized AI compute markets. The protocol functions as a full-stack decentralized compute infrastructure that transforms computational resources into verifiable, tokenized assets. Cysic Documentation
Core Architecture: Built on Cosmos CDK as a layer-1 blockchain using CometBFT BFT consensus, Cysic implements a novel Proof-of-Compute mechanism that incorporates both staked tokens and pledged computation into consensus. The system is structured as a modular stack with four layers: Hardware, Consensus, Execution, and Product layers. Cysic Documentation
Development Stage: Cysic has progressed through multiple testnet phases (Phase I launched July 2024, Phase II in progress) and transitioned to early mainnet in December 2025. Evidence includes active trading on major exchanges (Binance Alpha, Gate.io, Bitget), mainnet blockchain explorer functionality, and ongoing node operator recruitment. Cysic Medium
Team Capability Signals: GitHub activity shows ongoing development with recent updates to Jolt-B zkVM implementation (January 2026) and multiple active repositories for elliptic curves, finite field libraries, and ZK template libraries. The technical documentation demonstrates deep expertise in ZK cryptography and hardware acceleration. Cysic GitHub
2. System Architecture and Threat Model
Core Actors and Responsibilities
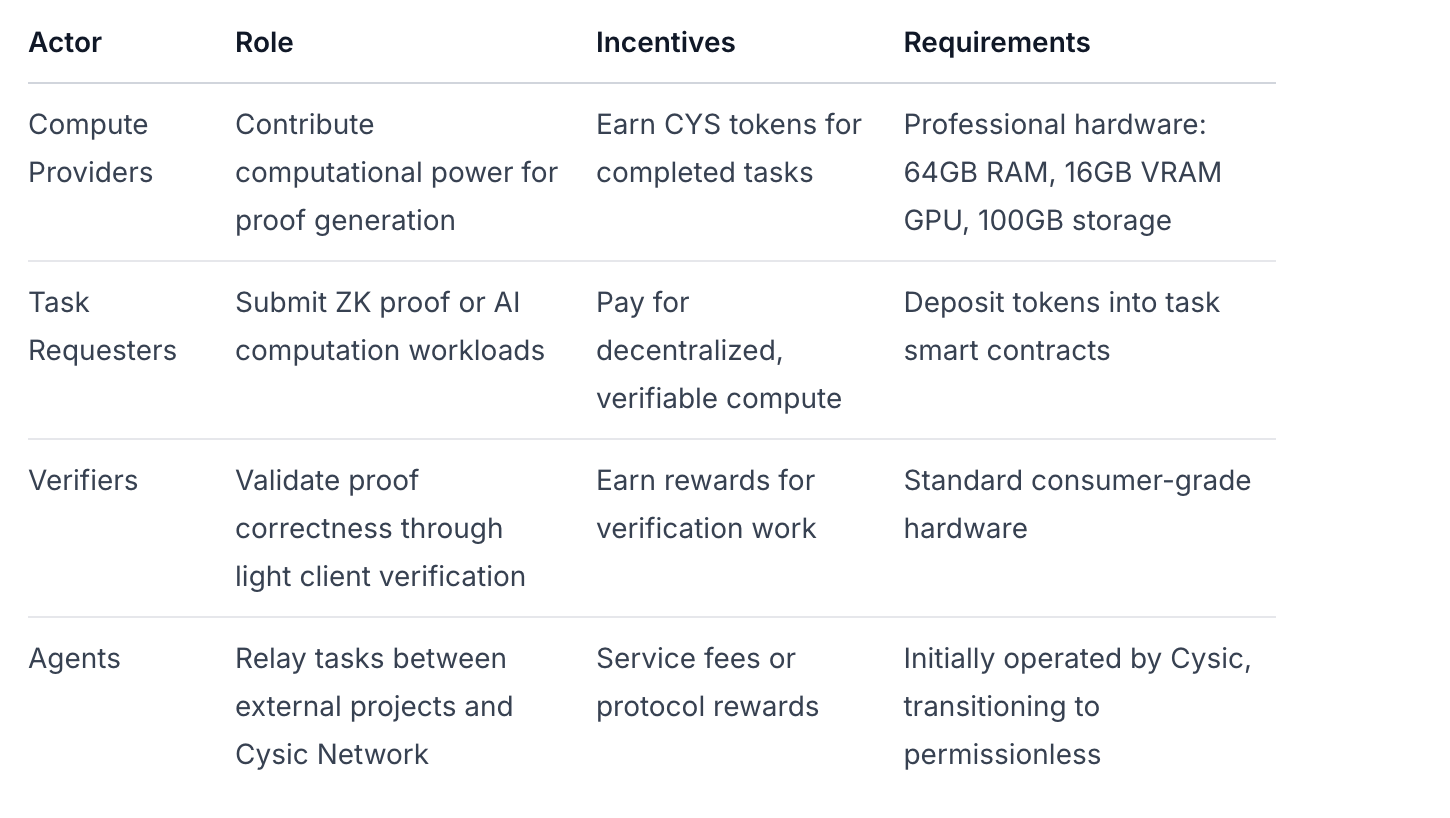
Architectural Components
The system employs a multi-layered approach:
Hardware Layer: Physical infrastructure including GPU servers, ASIC miners, and custom ZK acceleration hardware
Consensus Layer: Proof-of-Compute mechanism building on CometBFT BFT consensus
Execution Layer: Smart contracts for job scheduling, workload routing, and bridging
Product Layer: Domain-specific modules for ZK proving, AI inference, and mining workloads Cysic Documentation
Threat Model and Mitigations
Primary Threats:
Malicious Provers: Submitting invalid proofs to sabotage network or steal rewards
Mitigation: Cryptographic proof verification + redundancy (multiple provers per task) + staking slashing
Sybil Attacks: Creating multiple identities to game task allocation
Mitigation: Verifiable Random Function selection weighted by ve-token holdings
Collusion Attacks: Provers and verifiers coordinating to approve invalid proofs
Mitigation: Large validator committees (VCMs) with distributed voting + AVS services
Economic Attacks: Manipulating reward mechanisms or token economics
Mitigation: Time-locked vesting for team/investors, gradual DAO transition Cysic Whitepaper
The system explicitly assumes Byzantine conditions (up to 1/3 malicious nodes) and implements cryptographic verification, economic staking, and redundancy to maintain security.
3. Verifiable Compute and ZK Proof Infrastructure
Technical Implementation
Cysic supports multiple proof systems including Halo2, Plonky2, Gnark, and RapidSnark through both GPU acceleration and custom ASIC designs. The workflow follows a structured pipeline:
Task Submission: ZK projects deposit tokens and notify agent contracts
Prover Selection: Interested provers run VRF to determine eligibility (probability weighted by ve-tokens)
Proof Generation: Fastest three provers complete computation and update blockchain status
Verification: Larger validator committee verifies proofs through light client validation
Settlement: Valid proofs trigger reward distribution; invalid proofs trigger slashing Cysic ZK Layer
Performance Characteristics
The protocol addresses two fundamental ZK challenges:
Prover Decentralization: Avoids single points of failure while maintaining efficiency through hardware acceleration
Verification Cost/Latency: Uses two-stage settlement (off-chain verification + aggregated on-chain settlement) to balance cost and latency
Comparative Advantage: Unlike centralized prover services (e.g., traditional cloud providers), Cysic offers decentralized verification. Unlike rollup-native markets, Cysic provides hardware acceleration and cross-protocol support. The custom ASIC development (ZK C1 chip) promises 10-100× efficiency gains over GPU-based alternatives. Cysic Hardware
4. Hardware Coordination and Decentralized Compute Economy
Hardware Integration Strategy
Cysic employs a vertically integrated hardware stack:
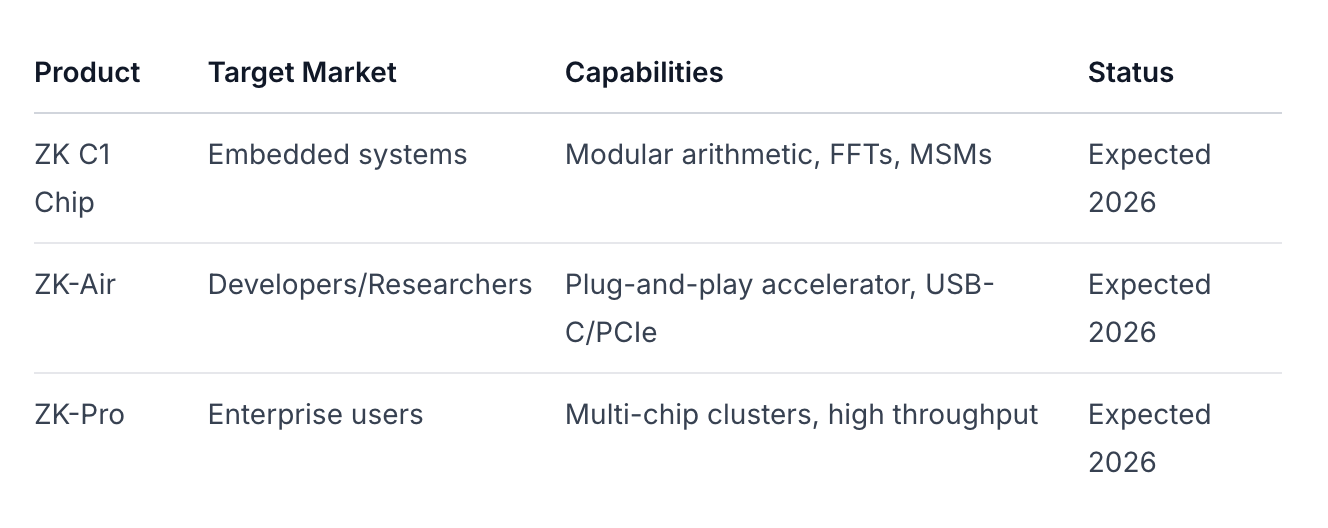
Minimum Requirements for Node Operators:
GPU Nodes: 64GB RAM, 16GB VRAM, 100GB storage, 8-core CPU
Consumer Verification: Standard hardware sufficient for light client duties Prover Guide
Economic Coordination
Compute resources are treated as yield-generating infrastructure assets rather than pure commodities. The coordination mechanism involves:
Task Matching: Marketplace matches workloads with providers based on performance, fairness, and reliability
Bidding System: Providers bid on tasks with adjustable pricing to maximize earnings
Performance-Based Rewards: Higher stake and better performance translate to improved task priority and earnings
Resource Normalization: Heterogeneous resources (GPU cycles, ASIC hashes, proof cycles) are normalized for comparable pricing
This approach creates capital efficiency through:
Utilization-based rewards rather than pure staking yields
Hardware flexibility (from consumer devices to data center systems)
Dynamic pricing based on supply-demand dynamics
5. Protocol Economics and Token Design
CYS Token Utility
The $CYS token (1 billion total supply) serves three primary functions:
Compute Access: Providers must reserve CYS to run provers, AI nodes, or computing tasks
Governance Rights: Staking CYS mints CGT (Cysic Governance Token) for voting on upgrades, parameters, and validator election
Reward Distribution: Compute providers earn CYS for supplying hardware; stakers earn for securing consensus
Token Allocation and Emission
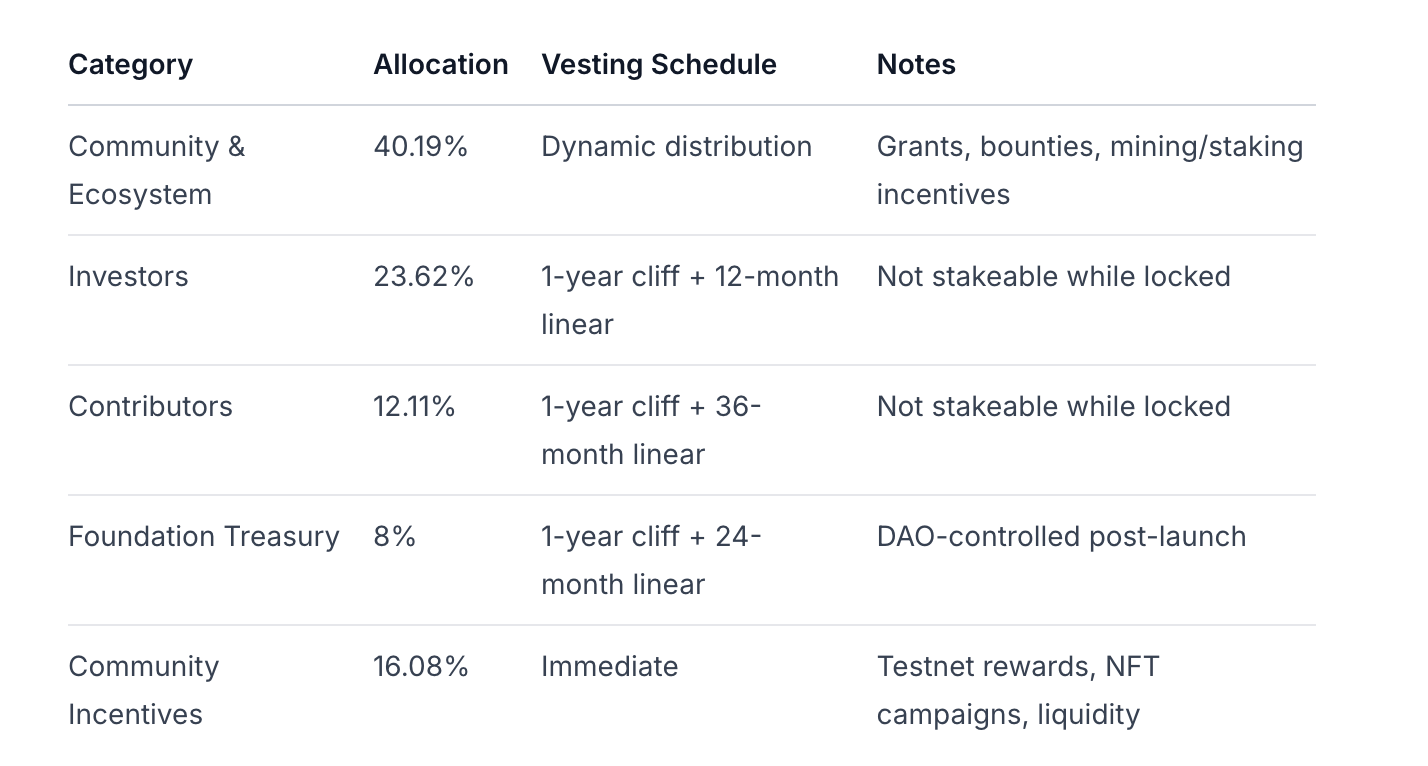
Economic Sustainability: Protocol revenue is directly tied to real compute demand through task fees rather than inflationary subsidies. However, the model remains sensitive to competition from both centralized cloud providers and alternative ZK networks on cost and performance metrics. Tokenomics
Current Market Position
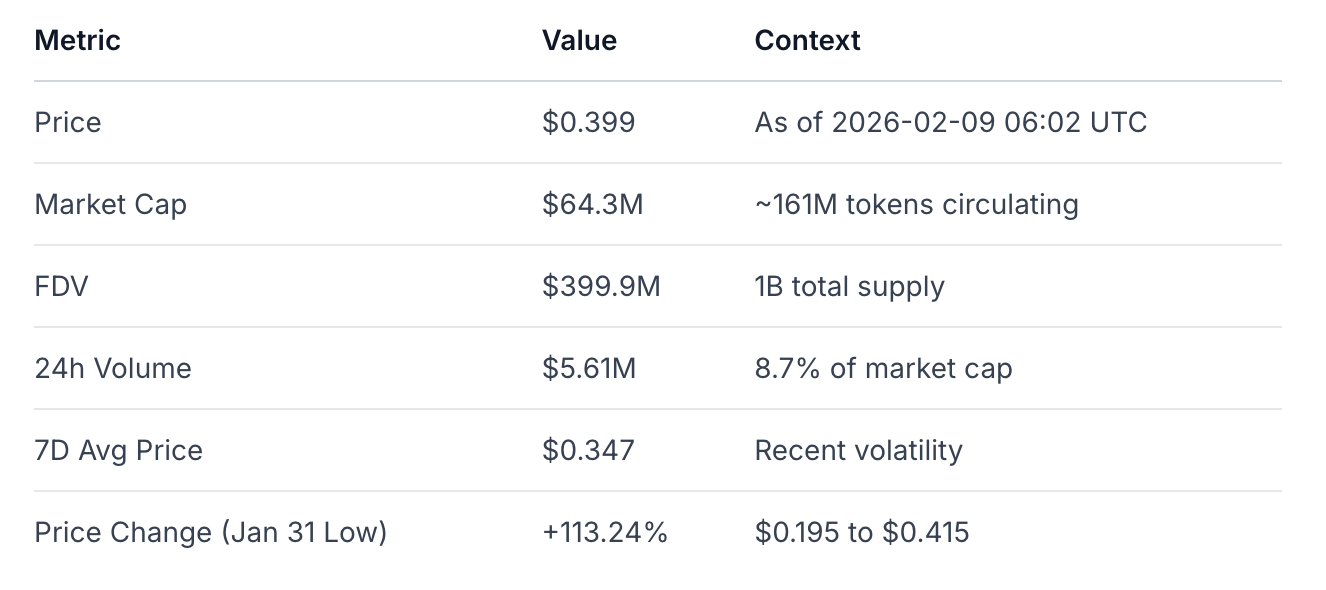
Exchange Listings: Active spot trading on Binance Alpha, Gate.io, Bitget, and Aster; some perpetual contracts delisted on Bybit and Bitget in January 2026, indicating exchange reassessment of market conditions. Market Data
6. Governance, Security, and Upgradeability
Governance Structure
Cysic implements a dual-token governance model:
CYS: The base token used for staking and compute access
CGT: Governance token minted through staking CYS, used for voting rights
Governance Controls:
Protocol upgrades and economic parameters
Block producer and validator node election
Community fund management and grant proposals
Treasury control (transitioning to DAO over time)
Security Considerations
Smart Contract Risk: As a Cosmos-based chain, Cysic inherits the security model of Cosmos SDK and CometBFT. The execution layer utilizes EVM-compatible smart contracts for coordination.
Cryptographic Risk: The protocol relies on established cryptographic primitives but implements custom hardware acceleration. The ZK C1 ASIC design introduces potential side-channel vulnerabilities that require rigorous security auditing.
Hardware Trust Assumptions: The vertical integration model creates dependence on Cysic's hardware security. Unlike pure software solutions, hardware vulnerabilities could require physical recalls or updates.
Failure Modes: Under adversarial conditions, the network could experience:
Task starvation if malicious actors dominate prover selection
Verification delays if validator committees are compromised
Economic instability if token volatility affects staking economics
7. Adoption Signals and Ecosystem Integration
Current Adoption Metrics
Network Activity:
7 million+ proofs generated historically (prior to mainnet launch)
23,000+ applicants for verifier program (20x available spots)
Active mainnet with blockchain explorer operational Cysic Explorer
Development Activity:
Regular GitHub commits across multiple repositories
Jolt-B zkVM implementation updated January 2026
Active documentation maintenance and updates Cysic GitHub
Strategic Partnerships
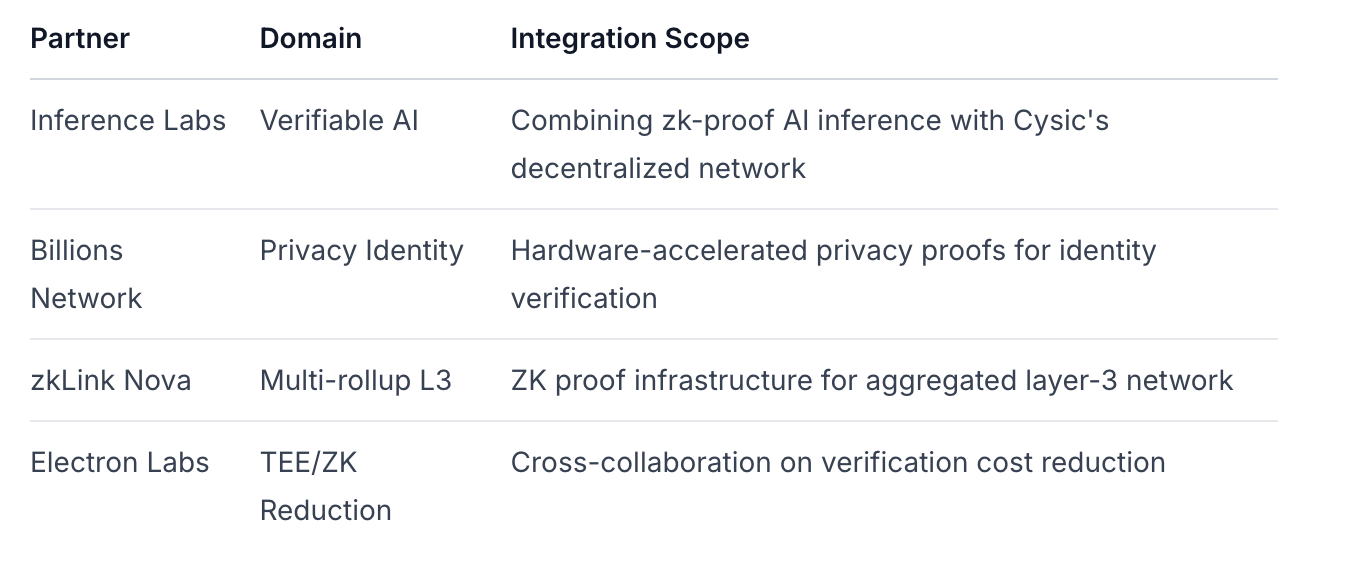
Use Case Prioritization: Near-term demand most likely from:
ZK Rollups: Scalable proof generation for Ethereum L2s
Verifiable AI: Auditable AI execution for financial and governance applications
Privacy Systems: Identity verification and privacy-preserving computations
8. Strategic Trajectory and Market Fit
Problem Solution Fit
Cysic addresses three structurally hard problems:
ZK Proof Centralization: Current proof generation is dominated by centralized services creating single points of failure and trust assumptions
AI Compute Trust Deficits: AI systems operate as black boxes without verifiable execution proofs
Cloud Compute Opacity: Traditional cloud computing lacks transparent pricing and verification mechanisms
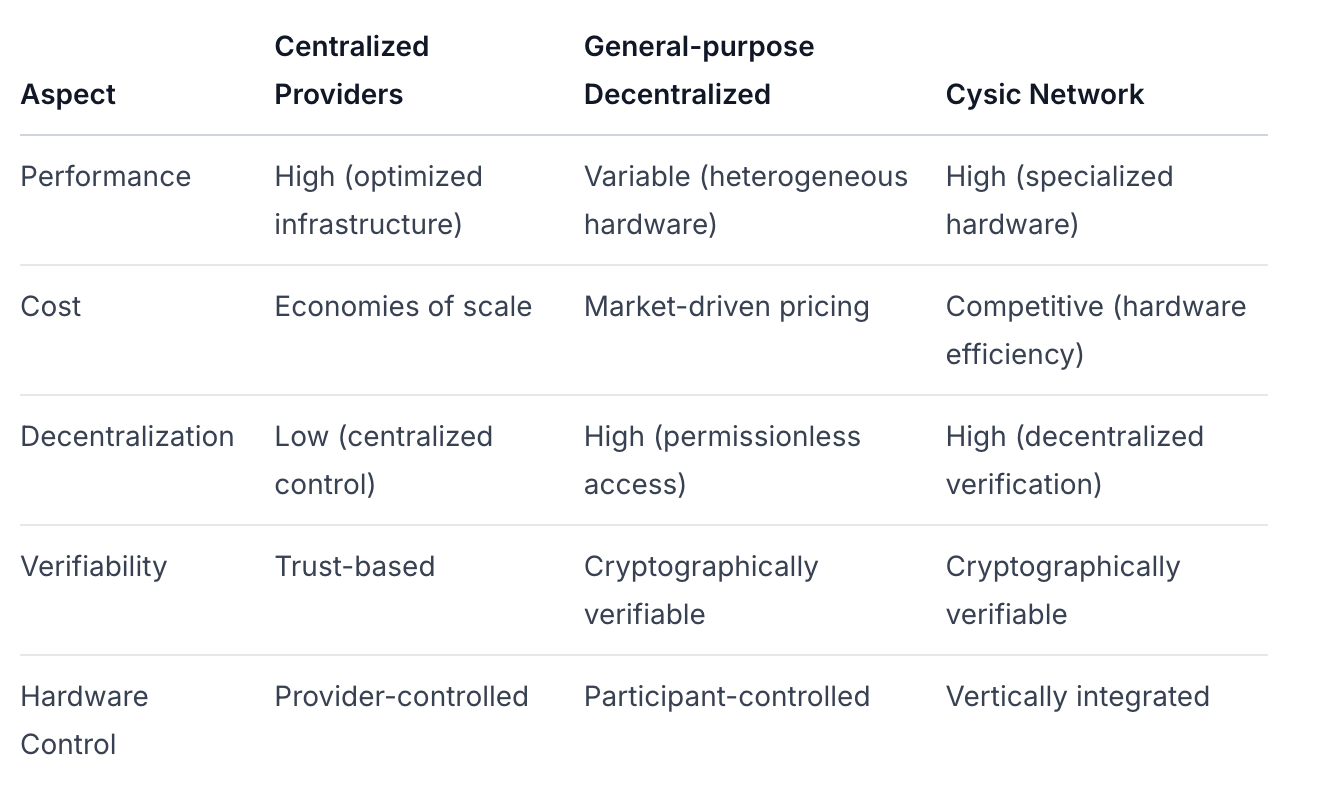
Competitive Landscape Analysis
Key Milestones (12-24 Month Horizon)
Hardware Deployment: Successful rollout of ZK-Air and ZK-Pro systems (2026)
Throughput Scaling: Achieving sustainable proof generation capacity for major rollups
Ecosystem Growth: Onboarding additional ZK and AI protocols as task requesters
DAO Transition: Full decentralization of governance and treasury management
9. Final Investment Assessment
Dimension Scoring (1-5 Scale)
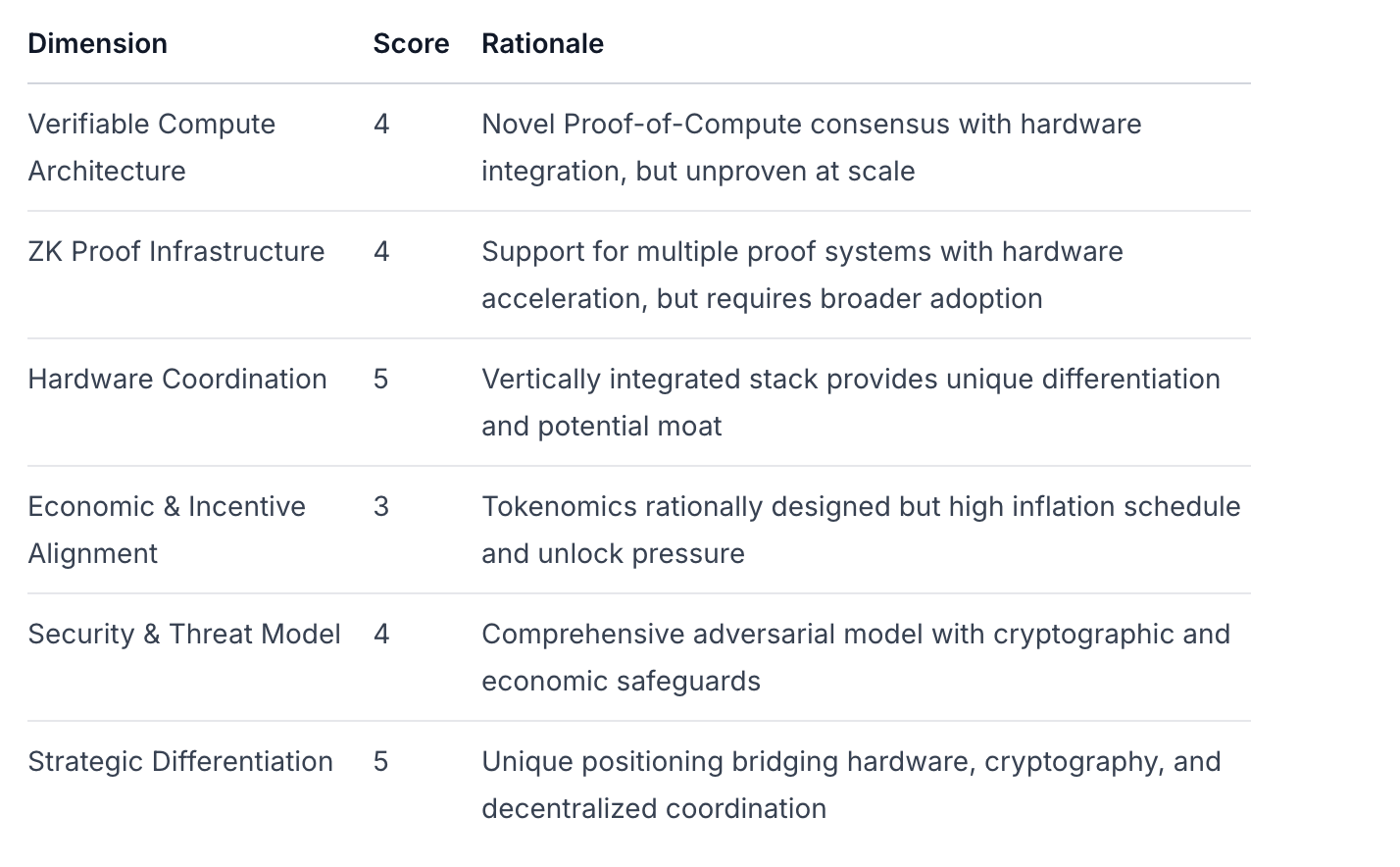
Overall Score: 4.2/5
Investment Verdict
Cysic Network presents a compelling investment opportunity for tier-1 crypto funds with a high-risk tolerance and long-time horizon. The protocol demonstrates genuine technical innovation through its vertically integrated approach to verifiable compute, addressing fundamental limitations in both ZK proof generation and AI computation trust.
Key Strengths:
Technical Differentiation: Hardware integration provides potential performance and cost advantages
Market Timing: Growing demand for verifiable compute from both crypto and traditional sectors
Team Execution: Demonstrated capability in delivering complex cryptographic systems
Community traction: Significant interest from both developers and node operators
Key Risks:
Execution Risk: Hardware development and deployment carries substantial technical and operational challenges
Market Risk: Requires simultaneous adoption from both compute providers and task requesters
Financial Risk: High FDV ($400M) relative to current adoption, with significant token unlocks ahead
Competitive Risk: Established cloud providers and well-funded crypto competitors targeting similar markets
Recommendation: Strategic monitoring with prepared allocation for milestone-based investment. The current valuation incorporates significant future success assumptions, but the protocol's technical differentiation and market position justify close attention. Investment should be contingent on: (1) Successful hardware deployment and performance metrics, (2) Growing task volume from reputable protocols, and (3) Sustainable economic model beyond inflationary rewards.
Cysic represents exactly the type of deep infrastructure play that could define the next generation of decentralized computation—if they can execute against their ambitious vision.
read more: https://www.kkdemian.com/blog/cysic_network_cys